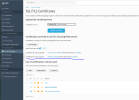
- Server operating system version
- Ubuntu 20.04.6 LTS
- Plesk version and microupdate number
- 18.0.56 Update #3
I'm trying to set up webmail in one of my domains, but neither horde nor roundcobe works. Both tell me connection to webserver fails.
some facts: webmail.my.domain is secured with LetsEncrypt, the config of i.e. roundcube looks like this:
any hints what/where to check?
some facts: webmail.my.domain is secured with LetsEncrypt, the config of i.e. roundcube looks like this:
Code:
$config['imap_host'] = 'ssl://localhost:993';
// IMAP authentication method (DIGEST-MD5, CRAM-MD5, LOGIN, PLAIN or null).
// Use 'IMAP' to authenticate with IMAP LOGIN command.
// By default the most secure method (from supported) will be selected.
$config['imap_auth_type'] = 'PLAIN';
// IMAP socket context options
// See http://php.net/manual/en/context.ssl.php
// The example below enables server certificate validation
//$config['imap_conn_options'] = [
// 'ssl' => [
// 'verify_peer' => true,
// 'verify_depth' => 3,
// 'cafile' => '/etc/openssl/certs/ca.crt',
// ],
// ];
// Note: These can be also specified as an array of options indexed by hostname
$config['imap_conn_options'] = array(
'ssl' => array(
'verify_peer' => false,
'verify_peer_name' => false,
'allow_self_signed' => true,
'crypto_method' => defined('STREAM_CRYPTO_METHOD_TLSv1_2_CLIENT')
? (STREAM_CRYPTO_METHOD_TLS_CLIENT
| @STREAM_CRYPTO_METHOD_TLSv1_1_CLIENT
| @STREAM_CRYPTO_METHOD_TLSv1_2_CLIENT)
: STREAM_CRYPTO_METHOD_SSLv23_CLIENT,
),
);any hints what/where to check?