Abdelkarim Mateos
New Pleskian
I read guide for Enabling DKIM
Yet I am amazed. Perhaps I have not understood the matter due to my difficulty with English.
DKIM is a typical signature system based on a public / private pair.
In all the servers that I work (cpanel, vesta, ISPConfig, without control panel or baremetal), the thing is simple.
One can have DNS installed, and use the facility of said panel to activate DKIM and have the panel create and use the pair of keys in order to sign outgoing emails.
In the chaos of not having a control panel, well, it's time to create the signature files, manually by SSH, but the question is the same and logical.
Good. On my client's server, DNS is activated since there are domains that use the DNS of that plesk, and others that use external DNS.
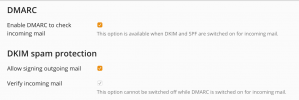
So, thanks for this, if we activate the DKIM in the xxxx.com domain, plesk creates two entries
With the data of both we can create or clone the zone record in our external DNS server.
This works on all the servers that I manage, except Plesk Obsidian and I find that their documentation tells me that the way that exists is to "turn off the dns" since otherwise plesk will sign the emails but the remote server will not be able to verify the shape.
Well, I must have gotten lost, because the remote mail server will never consult the signature with the plesk DNS, but with the domain delegated dns, where we already have the DKIM zone registry.
Certainly, I cannot find an explanation or solution to something as simple as using external DNS and DKIM.
Yet I am amazed. Perhaps I have not understood the matter due to my difficulty with English.
DKIM is a typical signature system based on a public / private pair.
In all the servers that I work (cpanel, vesta, ISPConfig, without control panel or baremetal), the thing is simple.
One can have DNS installed, and use the facility of said panel to activate DKIM and have the panel create and use the pair of keys in order to sign outgoing emails.
In the chaos of not having a control panel, well, it's time to create the signature files, manually by SSH, but the question is the same and logical.
- Create the public and private signature pair
- Configure the system so that the mail server signs outgoing mail
- Create the TXT record with the corresponding selector.
Good. On my client's server, DNS is activated since there are domains that use the DNS of that plesk, and others that use external DNS.
So, thanks for this, if we activate the DKIM in the xxxx.com domain, plesk creates two entries
- default._domainkey.
- _domainkey.
With the data of both we can create or clone the zone record in our external DNS server.
This works on all the servers that I manage, except Plesk Obsidian and I find that their documentation tells me that the way that exists is to "turn off the dns" since otherwise plesk will sign the emails but the remote server will not be able to verify the shape.
Well, I must have gotten lost, because the remote mail server will never consult the signature with the plesk DNS, but with the domain delegated dns, where we already have the DKIM zone registry.
Certainly, I cannot find an explanation or solution to something as simple as using external DNS and DKIM.