Alban Staehli
Regular Pleskian
- Server operating system version
- CentOS 7.9
- Plesk version and microupdate number
- 18.0.61
Hi,
Running Plesk Obsidian Version 18.0.61 on Centos 7.9.2009 (for the last week before moving to Alma) in a LXC in Proxmox.
Proxmox firewall enabled for the LXC, while iptable rules within the LXC works. From inside the Plesk LXC, if I add an iptable rule to block an IP , it actually does block the access.
As part of the apache badbot jail, I'm attempting to block Amazonbot as it does not respect robots.txt directives. The site is proxied via Cloudflare.
Fail2ban regex updated, reloaded, all good. I can now see its IP being listed as banned under Plesk UI.
Nevetherless, I also blocked via a nginx directive on the vhost itself, and still catches the connections from the meant to be blocked IP:
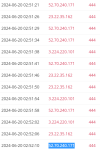
=> 52.70.240.171 being one of the IP
It's banned in Plesk:

I can see the ip being part of the f2b-BadBits chain in iptables
Chain f2b-BadBots (1 references)
target prot opt source destination
REJECT all -- 52.70.240.171 0.0.0.0/0 reject-with icmp-port-unreachable
I don't understand.
I verified as well that it catches custom bot and block access properly - no issue.
Any idea where shall I look?
Thanks.
Running Plesk Obsidian Version 18.0.61 on Centos 7.9.2009 (for the last week before moving to Alma) in a LXC in Proxmox.
Proxmox firewall enabled for the LXC, while iptable rules within the LXC works. From inside the Plesk LXC, if I add an iptable rule to block an IP , it actually does block the access.
As part of the apache badbot jail, I'm attempting to block Amazonbot as it does not respect robots.txt directives. The site is proxied via Cloudflare.
Fail2ban regex updated, reloaded, all good. I can now see its IP being listed as banned under Plesk UI.
Nevetherless, I also blocked via a nginx directive on the vhost itself, and still catches the connections from the meant to be blocked IP:

=> 52.70.240.171 being one of the IP
It's banned in Plesk:

I can see the ip being part of the f2b-BadBits chain in iptables
Chain f2b-BadBots (1 references)
target prot opt source destination
REJECT all -- 52.70.240.171 0.0.0.0/0 reject-with icmp-port-unreachable
I don't understand.
I verified as well that it catches custom bot and block access properly - no issue.
Any idea where shall I look?
Thanks.