Sergey K.
Basic Pleskian
CentOS Linux 8.5.2 , Plesk Obsidian Ver. 18.0.41
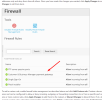
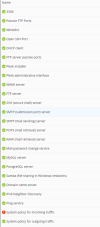
My server was attacked - DDoS,
I've protected 2 mains sites on server with CloudFlare, but hackers know my IP.
So, all other sites are down.
Could you advise how to close all additional ports to minimize server loading with help of some Plesk extension?
Any idea how to provide more power restrictions for this ?
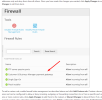
My server was attacked - DDoS,
I've protected 2 mains sites on server with CloudFlare, but hackers know my IP.
So, all other sites are down.
Could you advise how to close all additional ports to minimize server loading with help of some Plesk extension?
Any idea how to provide more power restrictions for this ?