Liwindo
Basic Pleskian
- Server operating system version
- Ubuntu 20.04.6 LTS
- Plesk version and microupdate number
- Plesk Obsidian v18.0.52_build1800230421.10 os_Ubuntu 20.04
As I needed to familiarise myself with the new Firewall App due to my issue I found some inconvenience I'd like to share.
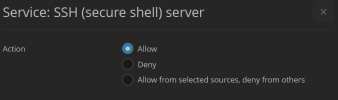
The following the image and code shows the standard setup provided by a new installed app:
I had the following findings:
1. The app blocks all incomming traffic which is not part of the mentioned services. So far so good but
2. It doesn't checks the real ports for these services or asks for input.
Example SSH: As it's a general security recommendation to change the standard port, on most systems it's a different one than 22. But the app directly blocks that service on other ports due to the rules since it only allows the traffic for the standard port 22.
3. How about the ports for other apps? Some of them have also ports which require incomming traffic. But when they're already installed and running why is the Firewall app not recognising that or that there is at least a dialog which is requesting for that before hard blocking it via the rule "System policy for incoming traffic -> Deny all other incoming traffic"?
The following the image and code shows the standard setup provided by a new installed app:

Bash:
#Starting deleted due to the hard limit of 10000 characters
# Start of /usr/sbin/iptables setup
/usr/sbin/iptables-save -t filter | grep -- "-A INPUT" | grep -v "fail2ban-\|f2b-" | sed -e "s#^-A#apply_rule /usr/sbin/iptables -D#g" | while read -r cmd; do ${cmd} || true; done
apply_rule /usr/sbin/iptables -F FORWARD
apply_rule /usr/sbin/iptables -F OUTPUT
apply_rule /usr/sbin/iptables -Z FORWARD
apply_rule /usr/sbin/iptables -Z OUTPUT
apply_rule /usr/sbin/iptables -P INPUT DROP
apply_rule /usr/sbin/iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp ! --syn -m state --state NEW -j REJECT --reject-with tcp-reset
apply_rule /usr/sbin/iptables -A INPUT -m state --state INVALID -j DROP
apply_rule /usr/sbin/iptables -P OUTPUT DROP
apply_rule /usr/sbin/iptables -A OUTPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
apply_rule /usr/sbin/iptables -A OUTPUT -p tcp ! --syn -m state --state NEW -j REJECT --reject-with tcp-reset
apply_rule /usr/sbin/iptables -A OUTPUT -m state --state INVALID -j DROP
apply_rule /usr/sbin/iptables -P FORWARD DROP
apply_rule /usr/sbin/iptables -A FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPT
apply_rule /usr/sbin/iptables -A FORWARD -p tcp ! --syn -m state --state NEW -j REJECT --reject-with tcp-reset
apply_rule /usr/sbin/iptables -A FORWARD -m state --state INVALID -j DROP
apply_rule /usr/sbin/iptables -A INPUT -i lo -j ACCEPT
apply_rule /usr/sbin/iptables -A OUTPUT -o lo -j ACCEPT
apply_rule /usr/sbin/iptables -A FORWARD -i lo -o lo -j ACCEPT
apply_rule /usr/sbin/iptables -t mangle -F
apply_rule /usr/sbin/iptables -t mangle -Z
apply_rule /usr/sbin/iptables -t mangle -P PREROUTING ACCEPT
apply_rule /usr/sbin/iptables -t mangle -P OUTPUT ACCEPT
apply_rule /usr/sbin/iptables -t mangle -P INPUT ACCEPT
apply_rule /usr/sbin/iptables -t mangle -P FORWARD ACCEPT
apply_rule /usr/sbin/iptables -t mangle -P POSTROUTING ACCEPT
apply_rule /usr/sbin/iptables -t nat -F
apply_rule /usr/sbin/iptables -t nat -Z
apply_rule /usr/sbin/iptables -t nat -P PREROUTING ACCEPT
apply_rule /usr/sbin/iptables -t nat -P OUTPUT ACCEPT
apply_rule /usr/sbin/iptables -t nat -P POSTROUTING ACCEPT
# Start of /usr/sbin/ip6tables setup
/usr/sbin/ip6tables-save -t filter | grep -- "-A INPUT" | grep -v "fail2ban-\|f2b-" | sed -e "s#^-A#apply_rule /usr/sbin/ip6tables -D#g" | while read -r cmd; do ${cmd} || true; done
apply_rule /usr/sbin/ip6tables -F FORWARD
apply_rule /usr/sbin/ip6tables -F OUTPUT
apply_rule /usr/sbin/ip6tables -Z FORWARD
apply_rule /usr/sbin/ip6tables -Z OUTPUT
apply_rule /usr/sbin/ip6tables -P INPUT DROP
apply_rule /usr/sbin/ip6tables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp ! --syn -m state --state NEW -j REJECT --reject-with tcp-reset
apply_rule /usr/sbin/ip6tables -A INPUT -m state --state INVALID -j DROP
apply_rule /usr/sbin/ip6tables -P OUTPUT DROP
apply_rule /usr/sbin/ip6tables -A OUTPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
apply_rule /usr/sbin/ip6tables -A OUTPUT -p tcp ! --syn -m state --state NEW -j REJECT --reject-with tcp-reset
apply_rule /usr/sbin/ip6tables -A OUTPUT -m state --state INVALID -j DROP
apply_rule /usr/sbin/ip6tables -P FORWARD DROP
apply_rule /usr/sbin/ip6tables -A FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPT
apply_rule /usr/sbin/ip6tables -A FORWARD -p tcp ! --syn -m state --state NEW -j REJECT --reject-with tcp-reset
apply_rule /usr/sbin/ip6tables -A FORWARD -m state --state INVALID -j DROP
apply_rule /usr/sbin/ip6tables -A INPUT -i lo -j ACCEPT
apply_rule /usr/sbin/ip6tables -A OUTPUT -o lo -j ACCEPT
apply_rule /usr/sbin/ip6tables -A FORWARD -i lo -o lo -j ACCEPT
apply_rule /usr/sbin/ip6tables -t mangle -F
apply_rule /usr/sbin/ip6tables -t mangle -Z
apply_rule /usr/sbin/ip6tables -t mangle -P PREROUTING ACCEPT
apply_rule /usr/sbin/ip6tables -t mangle -P OUTPUT ACCEPT
apply_rule /usr/sbin/ip6tables -t mangle -P INPUT ACCEPT
apply_rule /usr/sbin/ip6tables -t mangle -P FORWARD ACCEPT
apply_rule /usr/sbin/ip6tables -t mangle -P POSTROUTING ACCEPT
apply_rule /usr/sbin/ip6tables -t nat -F
apply_rule /usr/sbin/ip6tables -t nat -Z
apply_rule /usr/sbin/ip6tables -t nat -P PREROUTING ACCEPT
apply_rule /usr/sbin/ip6tables -t nat -P OUTPUT ACCEPT
apply_rule /usr/sbin/ip6tables -t nat -P POSTROUTING ACCEPT
# Start of /usr/sbin/iptables rules
apply_rule /usr/sbin/iptables -A INPUT -p udp --dport 68 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 49152:65535 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 8447 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 8443 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 8880 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 80 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 443 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 21 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 22 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 587 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 25 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 465 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 110 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 995 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 143 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 993 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 106 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 3306 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 5432 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p udp --dport 137 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p udp --dport 138 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 139 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 445 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p udp --dport 53 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p tcp --dport 53 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -p icmp --icmp-type 8/0 -j ACCEPT
apply_rule /usr/sbin/iptables -A INPUT -j DROP
apply_rule /usr/sbin/iptables -A OUTPUT -j ACCEPT
apply_rule /usr/sbin/iptables -A FORWARD -j DROP
# End of /usr/sbin/iptables rules
# Start of /usr/sbin/ip6tables rules
apply_rule /usr/sbin/ip6tables -A INPUT -p udp --dport 546 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 49152:65535 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 8447 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 8443 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 8880 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 80 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 443 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 21 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 22 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 587 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 25 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 465 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 110 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 995 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 143 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 993 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 106 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 3306 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 5432 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p udp --dport 137 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p udp --dport 138 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 139 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 445 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p udp --dport 53 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p tcp --dport 53 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p icmpv6 --icmpv6-type 130/0 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p icmpv6 --icmpv6-type 134/0 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p icmpv6 --icmpv6-type 135/0 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p icmpv6 --icmpv6-type 136/0 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p icmpv6 --icmpv6-type 137/0 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p icmpv6 --icmpv6-type 128/0 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -p icmpv6 --icmpv6-type 129/0 -j ACCEPT
apply_rule /usr/sbin/ip6tables -A INPUT -j DROP
apply_rule /usr/sbin/ip6tables -A OUTPUT -j ACCEPT
apply_rule /usr/sbin/ip6tables -A FORWARD -j DROPI had the following findings:
1. The app blocks all incomming traffic which is not part of the mentioned services. So far so good but
2. It doesn't checks the real ports for these services or asks for input.
Example SSH: As it's a general security recommendation to change the standard port, on most systems it's a different one than 22. But the app directly blocks that service on other ports due to the rules since it only allows the traffic for the standard port 22.
3. How about the ports for other apps? Some of them have also ports which require incomming traffic. But when they're already installed and running why is the Firewall app not recognising that or that there is at least a dialog which is requesting for that before hard blocking it via the rule "System policy for incoming traffic -> Deny all other incoming traffic"?