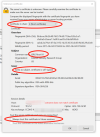
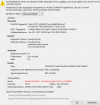
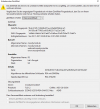
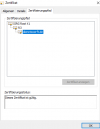
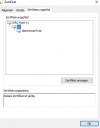
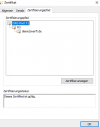
If you click "Certificate in Chain" and find that the Root certificate is DST Root CA X3 which expired on Sep 30, 2021, you are facing same issue as I was.
Here is how I solved the issue on my AWS Lightsail server, which is based on blueprint "Plesk Hosting Stack on Ubuntu":
A. On the server, I ran "
sudo su" to be a root user
B. Since my FTP server is ProFTPD, I ran "
cat /etc/proftd.conf" and find these lines:
TLSRSACertificateFile /opt/psa/admin/conf/httpsd.pem
TLSRSACertificateKeyFile /opt/psa/admin/conf/httpsd.pem
TLSCertificateChainFile /opt/psa/admin/conf/httpsd.pem
C. I ran "
/opt/psa/admin/conf/httpsd.pem" to find following 5 parts:
- CSR
- Private Key
- Server Certificate (expiry 3 months. Issuer is R3)
- R3 certificate (valid from Sep 3, 2020 to Sep 15, 2025. Issuer is ISRG Root X1)
- ISRG Root X1 certificate (valid is Jan 20, 2021 to Sep 30, 2024. Issuer is DST Root CA X3)
D. I copied and decoded above
5. ISRG Root X1 certificate with online certificate decoder. I found out that it was a certificate issued by the expired (Sep 30, 2021)
DST Root CA X 3 certificate. This is a wrong one and should be replaced by another self-issued
ISRG Root X1 certificate which is valid from Jun 4 ,2015 to Jun 4, 2035.
E. I downloaded the self-issued
ISRG Root X1 certificate from
https://letsencrypt.org/certs/isrgrootx1.pem then replace above
5. ISRG Root X1 certificate in file /opt/psa/admin/conf/httpsd.pem
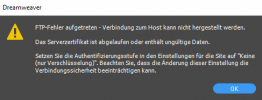
Now I run FileZilla Client to connect, I still get "Unknown certificate" alert. But the checkbox for "Always trust this certificate in future sessions" is enabled. I can check it to continue connection.
Hope it helps.