V
viktor
Guest
A Kernel flaw that has existed for over 10 years in the code has been discovered by Andrey Konovalov, a security researcher at Google. The DCCP (Datagram Congestion Control Protocol) implementation causes this flaw that can lead to kernel code execution from unprivileged processes. DCCP is a message-oriented transport layer protocol and enables the access to congestion-control mechanisms.
The good news first, the vulnerability is not executable remotely but requires a local account. The bad news is that a user can use the flaw to crash the system or escalate his privileges to get administrative access.
Andrey posted a detailed description about the bug:
In the current DCCP implementation an skb for a DCCP_PKT_REQUEST packet is forcibly freed via __kfree_skb in dccp_rcv_state_process if dccp_v6_conn_request successfully returns [3].
However, if IPV6_RECVPKTINFO is set on a socket, the address of the skb is saved to ireq->pktopts and the ref count for skb is incremented in dccp_v6_conn_request [4], so skb is still in use. Nevertheless, it still gets freed in dccp_rcv_state_process.
The fix is to call consume_skb, which accounts for skb->users, instead of doing goto discard and therefore calling __kfree_skb.
To exploit this double-free, it can be turned into a use-after-free:
// The first free:
kfree(dccp_skb)
// Another object allocated on the same place as dccp_skb:
some_object = kmalloc()
// The second free, effectively frees some_object
kfree(dccp_skb)
As this point, we have a use-after-free on some_object. An attacker can control what object that would be and overwrite its content with arbitrary data by using some of the kernel heap spraying techniques. If the overwritten object has any triggerable function pointers, an attacker gets to execute arbitrary code within the kernel.
Andrey already committed a patch for the DCCP flaw to the main Kernel code and all major Linux distributions already provide updates to fix this issue.
Use KernelCare for automatic, rebootless updates
KernelCare by CloudLinux will update your servers automatically without having to reboot the system. It ensures that your kernel is always up to date with all security updates and helps to lower operating costs for server management.
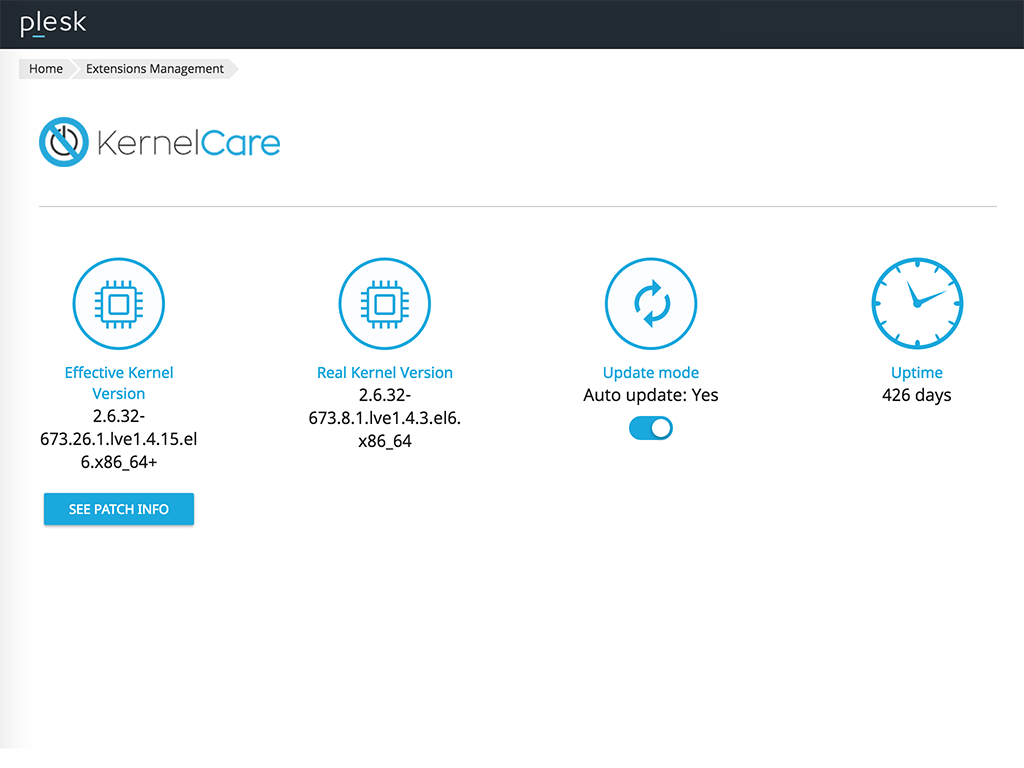
Keep your servers updated with the KernelCare Plesk extension that deploys kernel security patches, installed as soon as they are released to maintain the safest Linux environment!
Stay up-to-date and Plesky!
The post Critical Kernel flaw discovered – Update your server appeared first on Plesk.
Continue reading...
The good news first, the vulnerability is not executable remotely but requires a local account. The bad news is that a user can use the flaw to crash the system or escalate his privileges to get administrative access.
Andrey posted a detailed description about the bug:
In the current DCCP implementation an skb for a DCCP_PKT_REQUEST packet is forcibly freed via __kfree_skb in dccp_rcv_state_process if dccp_v6_conn_request successfully returns [3].
However, if IPV6_RECVPKTINFO is set on a socket, the address of the skb is saved to ireq->pktopts and the ref count for skb is incremented in dccp_v6_conn_request [4], so skb is still in use. Nevertheless, it still gets freed in dccp_rcv_state_process.
The fix is to call consume_skb, which accounts for skb->users, instead of doing goto discard and therefore calling __kfree_skb.
To exploit this double-free, it can be turned into a use-after-free:
// The first free:
kfree(dccp_skb)
// Another object allocated on the same place as dccp_skb:
some_object = kmalloc()
// The second free, effectively frees some_object
kfree(dccp_skb)
As this point, we have a use-after-free on some_object. An attacker can control what object that would be and overwrite its content with arbitrary data by using some of the kernel heap spraying techniques. If the overwritten object has any triggerable function pointers, an attacker gets to execute arbitrary code within the kernel.
Andrey already committed a patch for the DCCP flaw to the main Kernel code and all major Linux distributions already provide updates to fix this issue.
Use KernelCare for automatic, rebootless updates
KernelCare by CloudLinux will update your servers automatically without having to reboot the system. It ensures that your kernel is always up to date with all security updates and helps to lower operating costs for server management.

Keep your servers updated with the KernelCare Plesk extension that deploys kernel security patches, installed as soon as they are released to maintain the safest Linux environment!
Stay up-to-date and Plesky!
The post Critical Kernel flaw discovered – Update your server appeared first on Plesk.
Continue reading...
