- Server operating system version
- Debian 10
- Plesk version and microupdate number
- 18.0.49
Please help me.
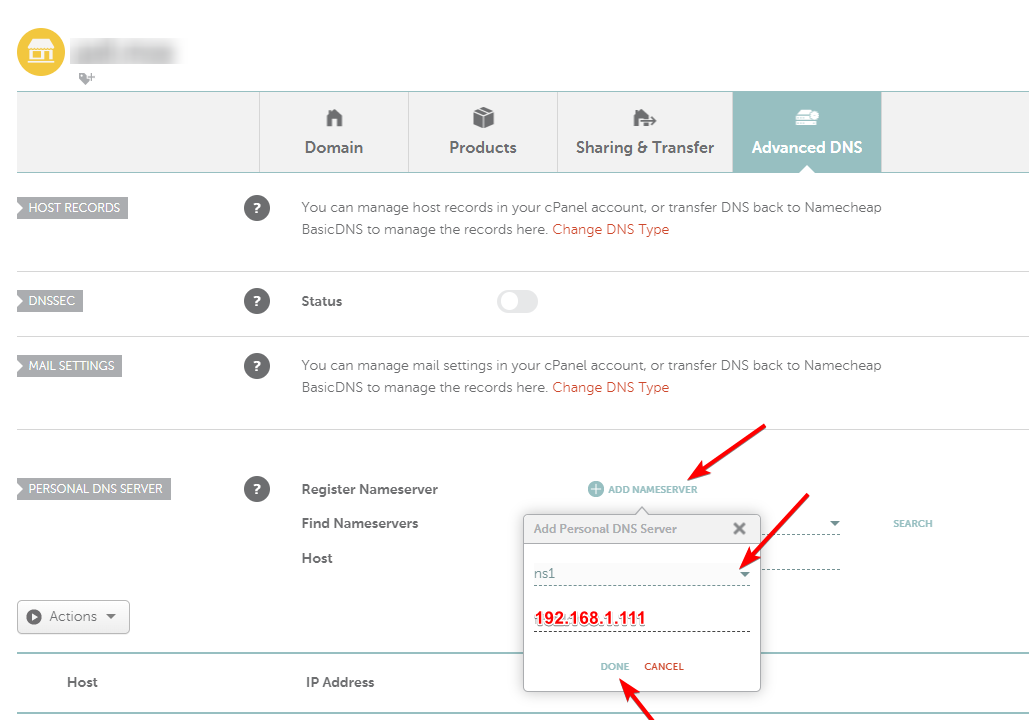
I have installed new Dedicated with Debian 10 and Plesk, my case is my site can't be reached, DNS issue, One or more of your nameservers did not respond.
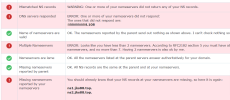
DNS Bind is running, firewall enable, port 53 open.
I have searched the same issue but I don't find solution for my case. Please help me.
I have installed new Dedicated with Debian 10 and Plesk, my case is my site can't be reached, DNS issue, One or more of your nameservers did not respond.

DNS Bind is running, firewall enable, port 53 open.
I have searched the same issue but I don't find solution for my case. Please help me.