TH-pleskuser
New Pleskian
Hi there,
after a few weeks now of trying myself, I could use some community help regarding explicit FTP over TLS. Allow me to describe my infrastructure
Physical Server, Debian with Proxmox 6.4-13
1 VM with Untangle Firewall, 2 network adapters (one int, one ext)
1 VM with Untangle Firewall, only for DNS on port 53
1 VM with Ubuntu 20.04 LTS and Plesk
I have followed this article:

 support.plesk.com
and this one:
support.plesk.com
and this one:

 support.plesk.com
support.plesk.com

 support.plesk.com
support.plesk.com
this is an extract of the FTP log:
And this is my filezilla:
my passive ports conf:
Below is the PROFTPD Config File. Note I have tried a different path to the certificates here and commented out the defaults (neither works). Both paths have the same files:
and here the actual config:
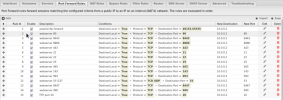
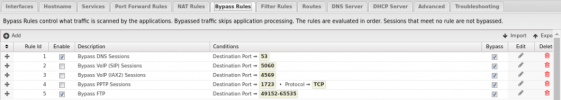
I am attaching the essential firewall rule screenshots, just to confirm the settings are in place. Really appreciate the community help here, thanks a million in advance for your suggestions!
after a few weeks now of trying myself, I could use some community help regarding explicit FTP over TLS. Allow me to describe my infrastructure
Physical Server, Debian with Proxmox 6.4-13
1 VM with Untangle Firewall, 2 network adapters (one int, one ext)
1 VM with Untangle Firewall, only for DNS on port 53
1 VM with Ubuntu 20.04 LTS and Plesk
- The Plesk VM is working just fine, I have production sites on it and the Untangle Firewall is doing what it is supposed, to port-forwarding everything that is needed, including the passive FTP port range.
- Plesk Firewall is disabled, as I use the VMs.
I have followed this article:

How to secure FTP (FTPS) in Plesk for Linux
Applicable to: Plesk for Linux Question How to configure secure FTP (FTPS) in Plesk for Linux? Answer Note: the below steps only make FTPS protocol available. Plesk does not manage FTPS mode set...

How to configure the passive ports range for ProFTPd on a Plesk server behind a firewall
Applicable to: Plesk for Linux Question How to configure the passive ports range for ProFTPd on a server behind a firewall? Answer Note: When configuring the passive port range, a selected port ...

How to secure FTP (FTPS) in Plesk for Linux
Applicable to: Plesk for Linux Question How to configure secure FTP (FTPS) in Plesk for Linux? Answer Note: the below steps only make FTPS protocol available. Plesk does not manage FTPS mode set...
this is an extract of the FTP log:
Code:
root@xxx:/var/log/plesk# tail -n20 ftp_tls.log
2021-08-28 10:21:52,679 mod_tls/2.9[1237139]: unable to accept TLS connection: system call error: [0] Success
2021-08-28 10:21:52,679 mod_tls/2.9[1237139]: TLS/TLS-C negotiation failed on control channel
2021-08-28 10:21:55,350 mod_tls/2.9[1237145]: TLS/TLS-C requested, starting TLS handshake
2021-08-28 10:22:15,720 mod_tls/2.9[1237145]: unable to accept TLS connection: system call error: [0] Success
2021-08-28 10:22:15,720 mod_tls/2.9[1237145]: TLS/TLS-C negotiation failed on control channel
2021-08-28 10:22:21,101 mod_tls/2.9[1237164]: TLS/TLS-C requested, starting TLS handshake
2021-08-28 10:22:41,416 mod_tls/2.9[1237164]: unable to accept TLS connection: system call error: [0] Success
2021-08-28 10:22:41,416 mod_tls/2.9[1237164]: TLS/TLS-C negotiation failed on control channel
2021-08-28 10:24:25,567 mod_tls/2.9[1237570]: TLS/TLS-C requested, starting TLS handshake
2021-08-28 10:24:45,781 mod_tls/2.9[1237570]: unable to accept TLS connection: system call error: [0] Success
2021-08-28 10:24:45,781 mod_tls/2.9[1237570]: TLS/TLS-C negotiation failed on control channel
2021-08-28 10:24:51,506 mod_tls/2.9[1237574]: TLS/TLS-C requested, starting TLS handshake
2021-08-28 10:25:11,678 mod_tls/2.9[1237574]: unable to accept TLS connection: system call error: [0] Success
2021-08-28 10:25:11,678 mod_tls/2.9[1237574]: TLS/TLS-C negotiation failed on control channel
2021-08-28 10:25:30,407 mod_tls/2.9[1237596]: TLS/TLS-C requested, starting TLS handshake
2021-08-28 10:25:50,671 mod_tls/2.9[1237596]: unable to accept TLS connection: system call error: [0] Success
2021-08-28 10:25:50,671 mod_tls/2.9[1237596]: TLS/TLS-C negotiation failed on control channel
2021-08-28 10:25:56,293 mod_tls/2.9[1237598]: TLS/TLS-C requested, starting TLS handshake
2021-08-28 10:26:16,447 mod_tls/2.9[1237598]: unable to accept TLS connection: system call error: [0] Success
2021-08-28 10:26:16,447 mod_tls/2.9[1237598]: TLS/TLS-C negotiation failed on control channelAnd this is my filezilla:
Code:
Status: Resolving address of xxx.xxx
Status: Connecting to 123.123.123.123:21...
Status: Connection established, waiting for welcome message...
Status: Initializing TLS...
Error: Connection timed out after 20 seconds of inactivity
Error: Could not connect to server
Status: Waiting to retry...my passive ports conf:
Code:
cat /etc/proftpd.d/55-passive-ports.conf
<Global>
PassivePorts 49152 65535
</Global>Below is the PROFTPD Config File. Note I have tried a different path to the certificates here and commented out the defaults (neither works). Both paths have the same files:
Code:
ls /usr/local/psa/admin/conf/
aps generated leika.conf panel.ini site_isolation_settings.ini templates
customizations.conf httpsd.pem openssl.cnf panel.ini.sample site_isolation_settings.ini.default
email_notification_template.html.sample httpsd.pem.sav openssl.input php.ini task-manager.yml.sample
ls /opt/psa/admin/conf/
aps generated leika.conf panel.ini site_isolation_settings.ini templates
customizations.conf httpsd.pem openssl.cnf panel.ini.sample site_isolation_settings.ini.default
email_notification_template.html.sample httpsd.pem.sav openssl.input php.ini task-manager.yml.sampleand here the actual config:
Code:
cat /etc/proftpd.conf
#
# To have more informations about Proftpd configuration
# look at : http://www.proftpd.org/
#
# This is a basic ProFTPD configuration file (rename it to
# 'proftpd.conf' for actual use. It establishes a single server
# and a single anonymous login. It assumes that you have a user/group
# "nobody" and "ftp" for normal operation and anon.
ServerName "ProFTPD"
#ServerType standalone
ServerType inetd
DefaultServer on
<Global>
DefaultRoot ~ psacln
AllowOverwrite on
# Prefer to put here directives allowed in server config and Global contexts.
# From http://www.proftpd.org/docs/howto/Vhost.html :
# "any configuration directives inside the "server config" section do not apply outside of the context."
DefaultTransferMode binary
UseFtpUsers on
TimesGMT off
SetEnv TZ :/etc/localtime
# Umask 022 is a good standard umask to prevent new dirs and files
# from being group and world writable.
Umask 022
# Primary log file mest be outside of system logrotate province.
TransferLog /var/log/plesk/xferlog
# Enable PAM authentication
AuthPAM on
AuthPAMConfig proftpd
AuthGroupFile /etc/group
<IfModule mod_ident.c>
IdentLookups off
</IfModule>
<IfModule mod_tls.c>
# common settings for all virtual hosts
TLSEngine on
TLSRequired off
TLSLog /var/log/plesk/ftp_tls.log
# DEBUGGING - REMOVED BY TH
# TLSRSACertificateFile /opt/psa/admin/conf/httpsd.pem
# TLSRSACertificateKeyFile /opt/psa/admin/conf/httpsd.pem
# TLSCertificateChainFile /opt/psa/admin/conf/httpsd.pem
TLSRSACertificateFile /usr/local/psa/admin/conf/httpsd.pem
TLSRSACertificateKeyFile /usr/local/psa/admin/conf/httpsd.pem
# Authenticate clients that want to use FTP over TLS?
TLSVerifyClient off
# Allow SSL/TLS renegotiations when the client requests them, but
# do not force the renegotations. Some clients do not support
# SSL/TLS renegotiations; when mod_tls forces a renegotiation, these
# clients will close the data connection, or there will be a timeout
# on an idle data connection.
TLSRenegotiate none
# As of ProFTPD 1.3.3rc1, mod_tls only accepts SSL/TLS data connections
# that reuse the SSL session of the control connection, as a security measure.
# Unfortunately, there are some clients (e.g. curl) which do not reuse SSL sessions.
TLSOptions NoSessionReuseRequired
</IfModule>
</Global>
# Port 21 is the standard FTP port.
Port 21
# To prevent DoS attacks, set the maximum number of child processes
# to 30. If you need to allow more than 30 concurrent connections
# at once, simply increase this value. Note that this ONLY works
# in standalone mode, in inetd mode you should use an inetd server
# that allows you to limit maximum number of processes per service
# (such as xinetd)
MaxInstances 30
#Following part of this config file were generate by PSA automatically
#Any changes in this part will be overwritten by next manipulation
#with Anonymous FTP feature in PSA control panel.
#Include directive should point to place where FTP Virtual Hosts configurations
#preserved
ScoreboardFile /var/run/proftpd.scoreboard
#Change default group for new files and directories in vhosts dir to psacln
<Directory /var/www/vhosts>
GroupOwner psacln
</Directory>
UseReverseDNS off
Include /etc/proftpd.d/*.confI am attaching the essential firewall rule screenshots, just to confirm the settings are in place. Really appreciate the community help here, thanks a million in advance for your suggestions!