raykai
Basic Pleskian
Hi,
I'm having a problem where Fail2ban is banning IPs of real bad visitors but as the bad users are coming in by Cloudflare proxy they can still hit my server on ports 80 and 443 even if I have Fail2ban blocking the IPs for all ports.
I restore the IPs from real visitors following this guide: https://support.plesk.com/hc/en-us/...behind-load-balancer-or-reverse-forward-proxy
I used the Server-wide solution with Nginx enabled option.
So in my logs do show the real IPs and not the IPs of Cloudflare. Fail2ban is listing and blocking the real visitor IPs but they can still connect to my server when I have Cloudflare proxy on.
I tested with having Cloudflare proxy off and it is blocking IPs correctly. But if I turn the Cloudflare proxy on I can hit my server even if the IP I'm using (VPN) is banned in Fail2ban.
Here is my Fail2Ban Filter:
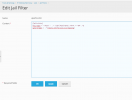
This is my Fail2Ban Jail:
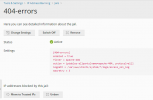
(note the max retry # is low just for testing.)
How can I get Fail2Ban to work correctly with Cloudflare?
I'm having a problem where Fail2ban is banning IPs of real bad visitors but as the bad users are coming in by Cloudflare proxy they can still hit my server on ports 80 and 443 even if I have Fail2ban blocking the IPs for all ports.
I restore the IPs from real visitors following this guide: https://support.plesk.com/hc/en-us/...behind-load-balancer-or-reverse-forward-proxy
I used the Server-wide solution with Nginx enabled option.
So in my logs do show the real IPs and not the IPs of Cloudflare. Fail2ban is listing and blocking the real visitor IPs but they can still connect to my server when I have Cloudflare proxy on.
I tested with having Cloudflare proxy off and it is blocking IPs correctly. But if I turn the Cloudflare proxy on I can hit my server even if the IP I'm using (VPN) is banned in Fail2ban.
Here is my Fail2Ban Filter:

This is my Fail2Ban Jail:

(note the max retry # is low just for testing.)
How can I get Fail2Ban to work correctly with Cloudflare?
