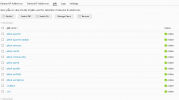
I have enabled fail2ban and most of the jails are working properly.
I have also enabled the recidive jail.
Alas, I often see messages like this in /var/log/maillog:
Apr 24 05:30:10 h2731888 postfix/smtpd[32272]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 05:41:49 h2731888 postfix/smtpd[4137]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 05:53:27 h2731888 postfix/smtpd[8381]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 06:05:11 h2731888 postfix/smtpd[12617]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 06:16:53 h2731888 postfix/smtpd[16348]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 06:28:18 h2731888 postfix/smtpd[20651]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 06:39:43 h2731888 postfix/smtpd[25252]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 06:51:07 h2731888 postfix/smtpd[29408]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 07:02:31 h2731888 postfix/smtpd[732]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 07:14:00 h2731888 postfix/smtpd[5328]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 07:25:20 h2731888 postfix/smtpd[9274]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
The postfix.conf filter seems not to match the above lines.
I found another filter in /etc/fail2ban/filter.d/postfix-sasl.local which does not seem to work either.
It has a failregex = ^%(__prefix_line)swarning: [-._\w]+\[<HOST>\]: SASL ((?i)LOGIN|PLAIN|(?:CRAM|DIGEST)-MD5) authentication failed [ A-Za-z0-9+/:]*={0,2})?\s*$ which does not match the log lines above.
[ A-Za-z0-9+/:]*={0,2})?\s*$ which does not match the log lines above.
Also I cannot find where this filter is enabled at all.
So my question is:
How can I get fail2ban to block those brute force SASL LOGIN attempts?
I have also enabled the recidive jail.
Alas, I often see messages like this in /var/log/maillog:
Apr 24 05:30:10 h2731888 postfix/smtpd[32272]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 05:41:49 h2731888 postfix/smtpd[4137]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 05:53:27 h2731888 postfix/smtpd[8381]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 06:05:11 h2731888 postfix/smtpd[12617]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 06:16:53 h2731888 postfix/smtpd[16348]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 06:28:18 h2731888 postfix/smtpd[20651]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 06:39:43 h2731888 postfix/smtpd[25252]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 06:51:07 h2731888 postfix/smtpd[29408]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 07:02:31 h2731888 postfix/smtpd[732]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 07:14:00 h2731888 postfix/smtpd[5328]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
Apr 24 07:25:20 h2731888 postfix/smtpd[9274]: warning: unknown[203.159.80.233]: SASL LOGIN authentication failed: authentication failure
The postfix.conf filter seems not to match the above lines.
I found another filter in /etc/fail2ban/filter.d/postfix-sasl.local which does not seem to work either.
It has a failregex = ^%(__prefix_line)swarning: [-._\w]+\[<HOST>\]: SASL ((?i)LOGIN|PLAIN|(?:CRAM|DIGEST)-MD5) authentication failed
Also I cannot find where this filter is enabled at all.
So my question is:
How can I get fail2ban to block those brute force SASL LOGIN attempts?
Last edited: