CoyoteKG
Regular Pleskian
Hi,
I know it is pretty simple to use Plesk firewall, but I need advice for 3 rules.
This is webserver with few sites, and access to SSH, FTP, MySQL I allowed only from few IP addresses.
Mail ports should be open, and also WWW.
I wan't to close everything else, but I'm not sure can I safely do that with
Domain name server Allow incoming from all
IPv6 Neighbor Discovery Allow incoming from all
Ping service Allow incoming from all
Should I block it, I believe that Ping and Neighbor discovery can with no problem, but what about DNS? What is purpose of this rule?
For domains for these websites hosted on server, I using nameservers from provider where we bought domains.
This is status of current iptables
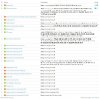
I know it is pretty simple to use Plesk firewall, but I need advice for 3 rules.
This is webserver with few sites, and access to SSH, FTP, MySQL I allowed only from few IP addresses.
Mail ports should be open, and also WWW.
I wan't to close everything else, but I'm not sure can I safely do that with
Domain name server Allow incoming from all
IPv6 Neighbor Discovery Allow incoming from all
Ping service Allow incoming from all
Should I block it, I believe that Ping and Neighbor discovery can with no problem, but what about DNS? What is purpose of this rule?
For domains for these websites hosted on server, I using nameservers from provider where we bought domains.
This is status of current iptables

