Mutate2546
New Pleskian
- Server operating system version
- CentOS 7.9.2009
- Plesk version and microupdate number
- 18.0.43
Hi there,
I've recently inherited some Plesk servers to manage. I'm pretty new with it, but I'm doing my best to understand it all. Bare with me, please
We use Plesk Obsidian Version 18.0.43 (CentOS Linux 7) which is hosted in a VM in Azure. To access all administrative interfaces & FTP we currently have our office network whitelisted to access FTP ports, Plesk-GUI, etc.
Willing to make access more secure and give flexibility to employees, our goal is to make administrative tasks available behind a VPN. I've managed to put the Administrative interface accessible thru it, but I'm having a hard time setting up FTP access.
Whenever I'm routing traffic thru my VPN, it communicates with the Plesk server via its private IP address, not the public one. Yet, according to what I've understood, whenever a Private & Public IP address is matched, all replies from my Plesk server (including FTP) return the public IP address causing an address mismatch, I believe.
Whenever I connect to the FTP via FileZilla from my office network, it works like a charm. Yet, whenever I route traffic via VPN, I receive an alert of SSL/TLS certificate saying that the "Hostname does not match certificate" (not sure if this can cause any issue) and it seems that FTP enters in passive mode.
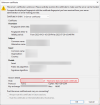
"xx,xx,xxx,xxx" = VPN private IP address
"yy,yy,yyy,yyy" = Public IP address
I've seen some other posts mentioning how to configure the Passive FTP (listed below), but it does not seem to work in my case (only if I'm missing something)
How to configure a passive ports range for ProFTPd on a server behind a firewall?
Unable to connect to FTP in passive mode
According to the documentations PassivePorts should be configured in
Even enabling kernel modules in system + restarting xinetd didn't work out.
No modification in the
I noticed as well that a file that was automatically generated by plesk in
zzz.zzz.zz.zz= Private IP adress
I do not have the Plesk firewall enabled. The only rule that I have it in my iptables (Firewalld is not enabled) is the f2b:
Chain INPUT (policy ACCEPT)
Chain f2b-plesk-proftpd (1 references)
I'm really lost where the problem can be. I wanted to make the FTP accessible from internal IP address and I don't see any way to do it. The firewall in Azure allows traffic between my VPN VM and Plesk server in all ports.
Sorry for the long post.
I've recently inherited some Plesk servers to manage. I'm pretty new with it, but I'm doing my best to understand it all. Bare with me, please
We use Plesk Obsidian Version 18.0.43 (CentOS Linux 7) which is hosted in a VM in Azure. To access all administrative interfaces & FTP we currently have our office network whitelisted to access FTP ports, Plesk-GUI, etc.
Willing to make access more secure and give flexibility to employees, our goal is to make administrative tasks available behind a VPN. I've managed to put the Administrative interface accessible thru it, but I'm having a hard time setting up FTP access.
Whenever I'm routing traffic thru my VPN, it communicates with the Plesk server via its private IP address, not the public one. Yet, according to what I've understood, whenever a Private & Public IP address is matched, all replies from my Plesk server (including FTP) return the public IP address causing an address mismatch, I believe.
Whenever I connect to the FTP via FileZilla from my office network, it works like a charm. Yet, whenever I route traffic via VPN, I receive an alert of SSL/TLS certificate saying that the "Hostname does not match certificate" (not sure if this can cause any issue) and it seems that FTP enters in passive mode.

"xx,xx,xxx,xxx" = VPN private IP address
"yy,yy,yyy,yyy" = Public IP address
Code:
Status: Resolving address of example.com
Status: Connecting to xxx.xx.xxx.xxx:21...
Status: Connection established, waiting for welcome message...
Status: Initializing TLS...
Status: TLS connection established.
Status: Logged in
Status: Retrieving directory listing...
Command: PWD
Response: 257 "/" is the current directory
Command: TYPE I
Response: 200 Type set to I
Command: PASV
Response: 227 Entering Passive Mode (yy,yy,yyy,yyy,236,80).
Command: MLSD
Error: Transfer connection interrupted: ECONNABORTED - Connection aborted
Error: Connection timed out after 20 seconds of inactivity
Error: Failed to retrieve directory listingI've seen some other posts mentioning how to configure the Passive FTP (listed below), but it does not seem to work in my case (only if I'm missing something)
How to configure a passive ports range for ProFTPd on a server behind a firewall?
Unable to connect to FTP in passive mode
According to the documentations PassivePorts should be configured in
/etc/proftpd.d/55-passive-ports.conf which is:
Code:
<Global>
PassivePorts 49152 65535
</Global>Even enabling kernel modules in system + restarting xinetd didn't work out.
No modification in the
/etc/proftpd.config as well.I noticed as well that a file that was automatically generated by plesk in
/etc/proftp.d/50-plesk.conf that does a MasqueradeAddress of my private IP and I don't know how and if I should remove it. zzz.zzz.zz.zz= Private IP adress
Code:
#ATTENTION!
#
#DO NOT MODIFY THIS FILE BECAUSE IT WAS GENERATED AUTOMATICALLY,
#SO YOUR CHANGES WILL BE LOST THE NEXT TIME THE FILE IS GENERATED.
# Global section
<Global>
RequireValidShell off
<IFModule mod_tls.c>
TLSEngine on
TLSRequired off
</IfModule>
</Global>
# Global Section
<VirtualHost zzz.zzz.zz.zz>
MasqueradeAddress yy.yy.yyy.yyy
</VirtualHost>I do not have the Plesk firewall enabled. The only rule that I have it in my iptables (Firewalld is not enabled) is the f2b:
iptables -LChain INPUT (policy ACCEPT)
| target | prot | opt | source | destination |
| f2b-plesk-proftpd | tcp | -- | anywhere | anywhere multiport dports ftp, ftp-data,ftps,ftps-data |
Chain f2b-plesk-proftpd (1 references)
| target | prot | opt | source | destination |
| f2b-plesk-proftpd | all | -- | anywhere | anywhere |
I'm really lost where the problem can be. I wanted to make the FTP accessible from internal IP address and I don't see any way to do it. The firewall in Azure allows traffic between my VPN VM and Plesk server in all ports.
Sorry for the long post.
