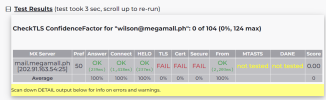
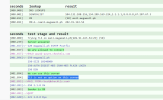
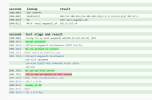
(cont.)
Feb 8 15:34:46 mail postfix/smtpd[8012]: private/rewrite socket: wanted attribute: flags
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute name: flags
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute value: 0
Feb 8 15:34:46 mail postfix/smtpd[8012]: private/rewrite socket: wanted attribute: address
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute name: address
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute value: ""
Feb 8 15:34:46 mail postfix/smtpd[8012]: private/rewrite socket: wanted attribute: (list terminator)
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute name: (end)
Feb 8 15:34:46 mail postfix/smtpd[8012]: rewrite_clnt: local: "" -> ""
Feb 8 15:34:46 mail postfix/smtpd[8012]: event_request_timer: reset 0x564b764896c5 0x564b76de8cc0 5
Feb 8 15:34:46 mail postfix/smtpd[8012]: send attr request = rewrite
Feb 8 15:34:46 mail postfix/smtpd[8012]: send attr rule = local
Feb 8 15:34:46 mail postfix/smtpd[8012]: send attr address =
[email protected]
Feb 8 15:34:46 mail postfix/smtpd[8012]: vstream_fflush_some: fd 28 flush 54
Feb 8 15:34:46 mail postfix/smtpd[8012]: vstream_buf_get_ready: fd 28 got 35
Feb 8 15:34:46 mail postfix/smtpd[8012]: private/rewrite socket: wanted attribute: flags
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute name: flags
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute value: 0
Feb 8 15:34:46 mail postfix/smtpd[8012]: private/rewrite socket: wanted attribute: address
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute name: address
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute value:
[email protected]
Feb 8 15:34:46 mail postfix/smtpd[8012]: private/rewrite socket: wanted attribute: (list terminator)
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute name: (end)
Feb 8 15:34:46 mail postfix/smtpd[8012]: rewrite_clnt: local:
[email protected] ->
[email protected]
Feb 8 15:34:46 mail postfix/smtpd[8012]: event_request_timer: reset 0x564b764896c5 0x564b76de8cc0 5
Feb 8 15:34:46 mail postfix/smtpd[8012]: send attr request = resolve
Feb 8 15:34:46 mail postfix/smtpd[8012]: send attr sender =
Feb 8 15:34:46 mail postfix/smtpd[8012]: send attr address =
[email protected]
Feb 8 15:34:46 mail postfix/smtpd[8012]: vstream_fflush_some: fd 28 flush 51
Feb 8 15:34:46 mail postfix/smtpd[8012]: vstream_buf_get_ready: fd 28 got 84
Feb 8 15:34:46 mail postfix/smtpd[8012]: private/rewrite socket: wanted attribute: flags
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute name: flags
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute value: 0
Feb 8 15:34:46 mail postfix/smtpd[8012]: private/rewrite socket: wanted attribute: transport
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute name: transport
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute value: smtp
Feb 8 15:34:46 mail postfix/smtpd[8012]: private/rewrite socket: wanted attribute: nexthop
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute name: nexthop
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute value: checktls.com
Feb 8 15:34:46 mail postfix/smtpd[8012]: private/rewrite socket: wanted attribute: recipient
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute name: recipient
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute value:
[email protected]
Feb 8 15:34:46 mail postfix/smtpd[8012]: private/rewrite socket: wanted attribute: flags
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute name: flags
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute value: 4096
Feb 8 15:34:46 mail postfix/smtpd[8012]: private/rewrite socket: wanted attribute: (list terminator)
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute name: (end)
Feb 8 15:34:46 mail postfix/smtpd[8012]: resolve_clnt: `' -> `
[email protected]' -> transp=`smtp' host=`checktls.com' rcpt=`
[email protected]' flags= class=default
Feb 8 15:34:46 mail postfix/smtpd[8012]: ctable_locate: install entry key ?
[email protected]
Feb 8 15:34:46 mail postfix/smtpd[8012]: extract_addr: in: <
[email protected]>, result:
[email protected]
Feb 8 15:34:46 mail postfix/smtpd[8012]: event_request_timer: reset 0x564b764896c5 0x564b76de8cc0 5
Feb 8 15:34:46 mail postfix/smtpd[8012]: send attr request = rewrite
Feb 8 15:34:46 mail postfix/smtpd[8012]: send attr rule = local
Feb 8 15:34:46 mail postfix/smtpd[8012]: send attr address = double-bounce
Feb 8 15:34:46 mail postfix/smtpd[8012]: vstream_fflush_some: fd 28 flush 50
Feb 8 15:34:46 mail postfix/smtpd[8012]: vstream_buf_get_ready: fd 28 got 48
Feb 8 15:34:46 mail postfix/smtpd[8012]: private/rewrite socket: wanted attribute: flags
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute name: flags
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute value: 0
Feb 8 15:34:46 mail postfix/smtpd[8012]: private/rewrite socket: wanted attribute: address
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute name: address
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute value:
[email protected]
Feb 8 15:34:46 mail postfix/smtpd[8012]: private/rewrite socket: wanted attribute: (list terminator)
Feb 8 15:34:46 mail postfix/smtpd[8012]: input attribute name: (end)
Feb 8 15:34:46 mail postfix/smtpd[8012]: rewrite_clnt: local: double-bounce ->
[email protected]
Feb 8 15:34:46 mail postfix/smtpd[8012]: report sender to all milters
Feb 8 15:34:46 mail postfix/smtpd[8012]: milter_macro_lookup: "i"
Feb 8 15:34:46 mail postfix/smtpd[8012]: milter_macro_lookup: "{auth_type}"
Feb 8 15:34:46 mail postfix/smtpd[8012]: milter_macro_lookup: "{auth_authen}"
Feb 8 15:34:46 mail postfix/smtpd[8012]: milter_macro_lookup: "{auth_author}"
Feb 8 15:34:46 mail postfix/smtpd[8012]: milter_macro_lookup: "{mail_addr}"
Feb 8 15:34:46 mail postfix/smtpd[8012]: ctable_locate: leave existing entry key ?
[email protected]
Feb 8 15:34:46 mail postfix/smtpd[8012]: milter_macro_lookup: result "
[email protected]"
Feb 8 15:34:46 mail postfix/smtpd[8012]: milter_macro_lookup: "{mail_host}"
Feb 8 15:34:46 mail postfix/smtpd[8012]: ctable_locate: leave existing entry key ?
[email protected]
Feb 8 15:34:46 mail postfix/smtpd[8012]: milter_macro_lookup: result "checktls.com"
Feb 8 15:34:46 mail postfix/smtpd[8012]: milter_macro_lookup: "{mail_mailer}"
Feb 8 15:34:46 mail postfix/smtpd[8012]: ctable_locate: leave existing entry key ?
[email protected]
Feb 8 15:34:46 mail postfix/smtpd[8012]: milter_macro_lookup: result "smtp"
Feb 8 15:34:46 mail postfix/smtpd[8012]: milter8_mail_event: milter inet:127.0.0.1:12768: mail <
[email protected]>
Feb 8 15:34:46 mail postfix/smtpd[8012]: event: SMFIC_MAIL; macros: {mail_addr}=
[email protected] {mail_host}=checktls.com {mail_mailer}=smtp
Feb 8 15:34:46 mail postfix/smtpd[8012]: vstream_fflush_some: fd 27 flush 105
Feb 8 15:34:46 mail postfix/smtpd[8012]: vstream_buf_get_ready: fd 27 got 5
Feb 8 15:34:46 mail postfix/smtpd[8012]: reply: SMFIR_CONTINUE data 0 bytes
Feb 8 15:34:46 mail postfix/smtpd[8012]: smtpd_check_rewrite: trying: permit_inet_interfaces
Feb 8 15:34:46 mail postfix/smtpd[8012]: permit_inet_interfaces: www12-azure.checktls.com 40.76.159.115
Feb 8 15:34:46 mail postfix/smtpd[8012]: fsspace: .: block size 4096, blocks free 8312605
Feb 8 15:34:46 mail postfix/smtpd[8012]: smtpd_check_queue: blocks 4096 avail 8312605 min_free 0 msg_size_limit 10240000
Feb 8 15:34:46 mail postfix/smtpd[8012]: > www12-azure.checktls.com[40.76.159.115]: 250 2.1.0 Ok
Feb 8 15:34:46 mail postfix/smtpd[8012]: watchdog_pat: 0x564b76db8840
Feb 8 15:34:46 mail postfix/smtpd[8012]: vstream_fflush_some: fd 25 flush 14
Feb 8 15:34:46 mail postfix/smtpd[8012]: vstream_buf_get_ready: fd 25 got 7
Feb 8 15:34:46 mail postfix/smtpd[8012]: < www12-azure.checktls.com[40.76.159.115]: QUIT
Feb 8 15:34:46 mail postfix/smtpd[8012]: > www12-azure.checktls.com[40.76.159.115]: 221 2.0.0 Bye