I have tried to check my website (which already has HTTP/3), but the result is "Peer reports incompatible or unsupported protocol version". Very strange, but to understand more, we need more details from the tool side.
Definitely not in your case, but some people, depending on their own testing devices' OS and its browsers' setups, may not be able to test for HTTP/3 (yet) but may not be aware that they can't... That then ends up with false test result for them, when they test their servers remotely using these devices / OS - AKA - People can / should setup & validate their browsers first (with browser HTTP/3 tests) and then run their own, remote server HTTP/3 tests, afterwards. The caveat here, is that they are not using any internet connection (i.e. ISP / Modem / Router etc) that does not allow or support HTTP/3.
We only use macOS / iOS devices, so can't comment on others, but having checked and configured browsers to suit in advance,
currently, Chrome (for Mac) always gives the most consistent, valid HTTP/3 test results for us. This will change, obviously, as HTTP/3 popularity increases / in general use everywhere.
Simple HTTP/3 browser tests can be run here:
https://http3.is/ (may need an initial refresh) and here:
https://quic.nginx.org/ (Top of the page, clear indication) and a detailed test can be run here:
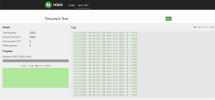
https://quic.nginx.org/quic.html just to be sure (attached image, tests taken on: iMac / Sonoma 14.5 / Chrome for macOS).
Once the OS browser is verified, those remote server HTTP/3 tests can be made here:
HTTP/3 Check here:
HTTP/3 Test | Ensure Your Website's Speed and Compatibility or via any of the methods (including api) detailed here:
How to Test if a Website Supports HTTP/3? Our own preferred test method is
not to use browsers, but to only to use Curl, which is consistent, detailed & 100% accurate. However, just for this post, we did run tests on our own servers using the aforementioned website:
Check Website Speed. Performance optimization made easy - GetPageSpeed and did achieve the correct HTTP/3 test results.