Hi,
on one of our SSD Servers, there was some Spam sending Problem last Week ago.
The Client had some Viruses on PC and Spammer logged in with Password on that Client Mailbox.
After we changed the Password, this Botnet permanently ran against this Mailbox and after 36 hours it looked like he stopped with attack.
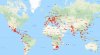
But today i saw it just got a little slower and we now nearly have 5k IP Adresses arround the World who trying to access that one Mailbox.
Does anyone has any Tipp what we can do? We already reported this to some federal buildings and yeah.
I can see that the Passwort Lengh is 9
Can i find out if they are using different Passwords / like brut Force? Or some other helpful informations?
We also setup some Lookup for Coordinates and Hosts and City ..... but we have Problems with Amounts of Ips comming together. I also stripped away duplicates. So these are real 5k IPs .....
Any Ideads what we can do?
Actually its not disturbing Server. Its about 10% CPU maybe little less than 10%......
on one of our SSD Servers, there was some Spam sending Problem last Week ago.
The Client had some Viruses on PC and Spammer logged in with Password on that Client Mailbox.
After we changed the Password, this Botnet permanently ran against this Mailbox and after 36 hours it looked like he stopped with attack.
But today i saw it just got a little slower and we now nearly have 5k IP Adresses arround the World who trying to access that one Mailbox.
Does anyone has any Tipp what we can do? We already reported this to some federal buildings and yeah.
I can see that the Passwort Lengh is 9
Can i find out if they are using different Passwords / like brut Force? Or some other helpful informations?
We also setup some Lookup for Coordinates and Hosts and City ..... but we have Problems with Amounts of Ips comming together. I also stripped away duplicates. So these are real 5k IPs .....
Code:
Sep 12 11:53:10 ssd plesk_saslauthd[18018]: failed mail authentication attempt for user '[email protected]' (password len=9)
Sep 12 11:53:10 ssd postfix/smtpd[3987]: warning: SASL authentication failure: Password verification failed
Sep 12 11:53:10 ssd postfix/smtpd[3987]: warning: unknown[180.244.233.175]: SASL PLAIN authentication failed: authentication failure
Sep 12 11:53:11 ssd postfix/smtpd[3987]: lost connection after AUTH from unknown[180.244.233.175]
Sep 12 11:53:11 ssd postfix/smtpd[3987]: disconnect from unknown[180.244.233.175]Any Ideads what we can do?
Actually its not disturbing Server. Its about 10% CPU maybe little less than 10%......