- Server operating system version
- Windows Server 2019
- Plesk version and microupdate number
- .
We have a Plesk under Window Server and is running behind Reverse Proxy server.
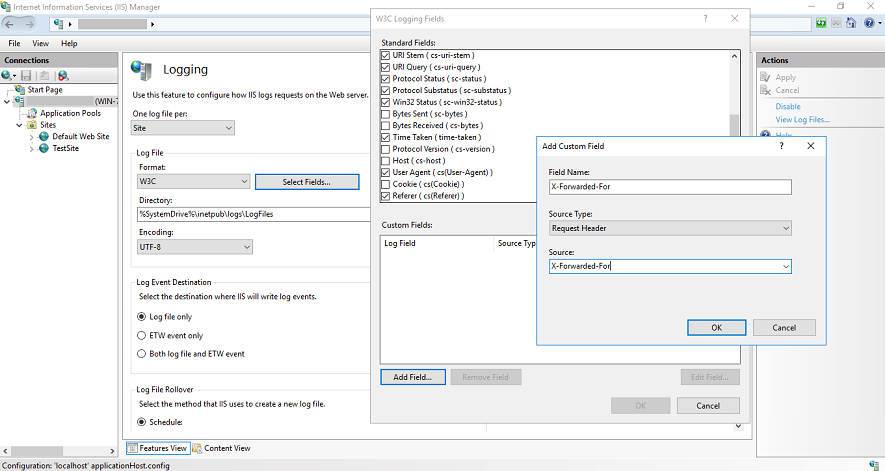
We would like to log the real public IP of web visitors, but all we can see is the Internal IP of Reverse Proxy Server.
I'm thinking that x-forwarded-for or other x-headers could resolve it. Tried to lookup some official guide but all I can see are for Nginx and Apache.
Similar to this one:
 www.plesk.com
www.plesk.com
Not really sure if this is the similar solution for Windows Plesk. Hope anyone from this community could provide insight on how.
We would like to log the real public IP of web visitors, but all we can see is the Internal IP of Reverse Proxy Server.
I'm thinking that x-forwarded-for or other x-headers could resolve it. Tried to lookup some official guide but all I can see are for Nginx and Apache.
Similar to this one:
Incorrect IP addresses logged by Plesk behind load balancer, or reverse/forward proxy - Support Cases from Plesk Knowledge Base
Incorrect IP addresses logged by Plesk behind load balancer, or reverse/forward proxy - Support Cases - Plesk Knowledge Base
 www.plesk.com
www.plesk.com
Not really sure if this is the similar solution for Windows Plesk. Hope anyone from this community could provide insight on how.