Brownsugar
New Pleskian
This problem has affected me for a long time.
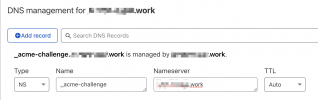
I have some domains that use the DNS managed by CloudFlare, so Let's Encrypt extension can't modify the TXT record when renewing the wildcard certs.
Any solution for this? Thanks.
I have some domains that use the DNS managed by CloudFlare, so Let's Encrypt extension can't modify the TXT record when renewing the wildcard certs.
Any solution for this? Thanks.
Last edited: