ChristophRo
Regular Pleskian
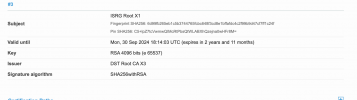
Guys, just be aware that even newly issued LetsEncrypt certificates are still dual/cross-signed with the old and now expired R3 certificate and a properly configured server will send this expired intermediate to the client. (alongside the domain certificate and the proper/new intermediate )
This can and will cause troubles with some clients, as they may check and use the old but not the new chain. (clients with older openssl library for example)
On the server side you can manually remove the old chain cert from the LetsEncrypt chain.pem/fullchain.pem files and this will solve that problem.
Of course, once the certificate gets renewed, you have to do this again...
Though I think that LetsEncrypt will stop cross-signing soon and this will solve the problem once and for all. (as it's completely bullshit to do so - at least now, that the old intermediate and root are expired)
This can and will cause troubles with some clients, as they may check and use the old but not the new chain. (clients with older openssl library for example)
On the server side you can manually remove the old chain cert from the LetsEncrypt chain.pem/fullchain.pem files and this will solve that problem.
Of course, once the certificate gets renewed, you have to do this again...
Though I think that LetsEncrypt will stop cross-signing soon and this will solve the problem once and for all. (as it's completely bullshit to do so - at least now, that the old intermediate and root are expired)