- Server operating system version
- CentOS Linux 7.9.2009 (Core)
- Plesk version and microupdate number
- Plesk Obsidian 18.0.48
Hi all,
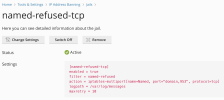
during last days I checked Log Browser and I find lot of this messages:
For example, from 10/11/2022 00:00:02 to 10/11/2022 00:48:15 I have got exactly 1.000 requests. All messages are identical differing only by IP address.
I checked and I have got requests from 47 different IP address. One IP address have made 2 requests, another 67, another 7, and this considering only one hour this night.
I checked and all IP are reported to AbuseIP portal.
My question is: should I block this kind of request? If I block them, I'll save resources?
Furthermore, anyone could explain me what type of requests are and why them are made?
Thank you in advance, I appreciate your support.
Marco
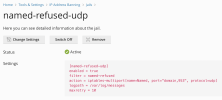
during last days I checked Log Browser and I find lot of this messages:
| 2022-11-10 11:13:15 | INFO | named [8769] System daemons [3] | client @0x7fcbc81063a0 [ip]#53 (sl): query (cache) 'sl/ANY/IN' denied |
For example, from 10/11/2022 00:00:02 to 10/11/2022 00:48:15 I have got exactly 1.000 requests. All messages are identical differing only by IP address.
I checked and I have got requests from 47 different IP address. One IP address have made 2 requests, another 67, another 7, and this considering only one hour this night.
I checked and all IP are reported to AbuseIP portal.
My question is: should I block this kind of request? If I block them, I'll save resources?
Furthermore, anyone could explain me what type of requests are and why them are made?
Thank you in advance, I appreciate your support.
Marco