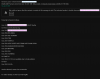
Jun 26 03:50:04 li1486-98 dovecot: pop3-login: Aborted login (no auth attempts in 0 secs): user=<>, rip=127.0.0.1, lip=127.0.0.1, secured, session=<9xexmvSo5LJ/AAAB>
Jun 26 03:50:04 li1486-98 dovecot: imap-login: Aborted login (no auth attempts in 0 secs): user=<>, rip=127.0.0.1, lip=127.0.0.1, TLS, session=<XlKxmvSorot/AAAB>
Jun 26 03:50:04 li1486-98 dovecot: imap-login: Aborted login (no auth attempts in 0 secs): user=<>, rip=127.0.0.1, lip=127.0.0.1, secured, session=<FH2xmvSosIx/AAAB>
Jun 26 03:55:04 li1486-98 dovecot: pop3-login: Aborted login (no auth attempts in 0 secs): user=<>, rip=127.0.0.1, lip=127.0.0.1, TLS, session=<fu+TrPSoAKR/AAAB>
Jun 26 03:55:04 li1486-98 dovecot: pop3-login: Aborted login (no auth attempts in 0 secs): user=<>, rip=127.0.0.1, lip=127.0.0.1, secured, session=<fhmUrPSoHrN/AAAB>
Jun 26 03:55:04 li1486-98 dovecot: imap-login: Aborted login (no auth attempts in 0 secs): user=<>, rip=127.0.0.1, lip=127.0.0.1, TLS, session=<Y1GUrPSo6It/AAAB>
Jun 26 03:55:04 li1486-98 dovecot: imap-login: Aborted login (no auth attempts in 0 secs): user=<>, rip=127.0.0.1, lip=127.0.0.1, secured, session=<LnqUrPSo6ox/AAAB>