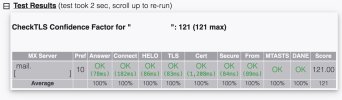
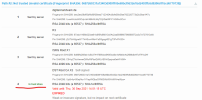
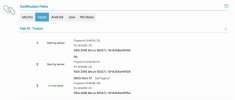
I have a problem that has been bothering me for a few days. I'm running a mail server with Plesk that establishes connections over port 465 with SSL/TLS encryption and over port 587 via STARTTLS (which is considered error prone and insecure). Since I don't actually allow the connection over port 587 and only opened it because of my current issue, I'm looking for help here for my problem.
When I set up a mail account in iOS or iPadOS, it takes about 5 minutes to connect / check settings before a connection is established to the mail server via port 465. If I use port 587 the verification is completed immediately. I do not have this problem when connecting to other systems / clients. Even on my MacBook Pro with Apple Mail or Postbox (Thunderbird offshoot), I can successfully and quickly establish a connection via port 465 to my mail server. Therefore, I think I can rule out a basic misconfiguration of the mail server.
Does anyone have the same problems or maybe tips on how I find out what exactly the problem is?
When I set up a mail account in iOS or iPadOS, it takes about 5 minutes to connect / check settings before a connection is established to the mail server via port 465. If I use port 587 the verification is completed immediately. I do not have this problem when connecting to other systems / clients. Even on my MacBook Pro with Apple Mail or Postbox (Thunderbird offshoot), I can successfully and quickly establish a connection via port 465 to my mail server. Therefore, I think I can rule out a basic misconfiguration of the mail server.
Does anyone have the same problems or maybe tips on how I find out what exactly the problem is?