- Server operating system version
- Ubuntu 20.04.6 LTS
- Plesk version and microupdate number
- 18.0.54
Hello,
since today my website started to be unresponsive.
Every few requests the website takes forever to load (30+ sec). Sometimes it shows a CF 524 - timeout error after 30 or 60sec and then loads the website.
Sometimes it loads for 10-15 sec and after pressing F5 lets the website load instantly.
I changed nothing on the website, nor did I update Plesk or something else.
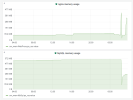
I noticed that before this issue happened, the Memory Usage dropped significantly, especially the MySQL memory usage halved. Nginx memory usage on the other hand 5x for a short period and is now tripled.
since today my website started to be unresponsive.
Every few requests the website takes forever to load (30+ sec). Sometimes it shows a CF 524 - timeout error after 30 or 60sec and then loads the website.
Sometimes it loads for 10-15 sec and after pressing F5 lets the website load instantly.
I changed nothing on the website, nor did I update Plesk or something else.
I noticed that before this issue happened, the Memory Usage dropped significantly, especially the MySQL memory usage halved. Nginx memory usage on the other hand 5x for a short period and is now tripled.

