Hello,
I have activated TLSv1.2 and TLSv1.3 on my Server. I use apache and nginx reverse proxy. I have followed this article to meet pci-dss compliance with Plesk Obisidian Version 18.0.27 on CentOS Linux 7.8.2003 (Core) Tune Plesk to Meet PCI DSS on Linux
Disabling weak SSL/TLS ciphers and protocols for the following Services:
plesk sbin pci_compliance_resolver --enable
- panel
- apache
- dovecot
- postfix
- proftpd
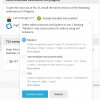
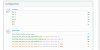
When I now check with SSL Labs, the Ciphers for TLSv1.3 are ok, but for TLSv1.2 are weak, please see screenshots.
I was asuming if running the pci_compliance_resolver for the services , that the Ciphers would be updated from weak to a secure level? Why Weak Ciphers for TLSv1.2 are still present on the server, how can I change this now, for all services ?
As I also use Nginx as Reverse Proxy, do I have to change there also something?
Thx
I have activated TLSv1.2 and TLSv1.3 on my Server. I use apache and nginx reverse proxy. I have followed this article to meet pci-dss compliance with Plesk Obisidian Version 18.0.27 on CentOS Linux 7.8.2003 (Core) Tune Plesk to Meet PCI DSS on Linux
Disabling weak SSL/TLS ciphers and protocols for the following Services:
plesk sbin pci_compliance_resolver --enable
- panel
- apache
- dovecot
- postfix
- proftpd
When I now check with SSL Labs, the Ciphers for TLSv1.3 are ok, but for TLSv1.2 are weak, please see screenshots.
I was asuming if running the pci_compliance_resolver for the services , that the Ciphers would be updated from weak to a secure level? Why Weak Ciphers for TLSv1.2 are still present on the server, how can I change this now, for all services ?
As I also use Nginx as Reverse Proxy, do I have to change there also something?
Thx