- Server operating system version
- Debian 11.8
- Plesk version and microupdate number
- 18.0.56
Hello,
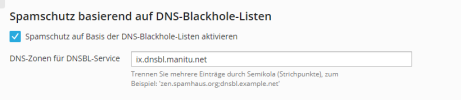
We are receiving a lot of spam in our servers in the last days/months. It seems that backlist like b.barracudacentral.org, bl.spamcop.net or zen.spamhaus.org does not stop the spam we received and spamassassin is good but a lot of spam is coming.
So I want to know what are you doing to stop the incoming spam in a plesk server.
Thanks a lot.
Regards
We are receiving a lot of spam in our servers in the last days/months. It seems that backlist like b.barracudacentral.org, bl.spamcop.net or zen.spamhaus.org does not stop the spam we received and spamassassin is good but a lot of spam is coming.
So I want to know what are you doing to stop the incoming spam in a plesk server.
Thanks a lot.
Regards