Hi Peter,
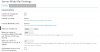
I get an other one, please see here the header information. mydomain and myservername.cloud are both correct in the send emails...., that's why its scary
Return-Path: <
[email protected]>
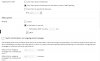
X-Spam-Checker-Version: SpamAssassin 3.4.0 (2014-02-07) on
myservername.cloud
X-Spam-Level:
X-Spam-Status: No, score=-89.3 required=7.0 tests=BITCOIN_EXTORT_01,
BITCOIN_SPAM_02,DKIM_SIGNED,DKIM_VALID,DKIM_VALID_AU,KHOP_DYNAMIC,RCVD_IN_PBL,
RCVD_IN_XBL,USER_IN_WHITELIST autolearn=no autolearn_force=no version=3.4.0
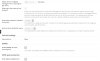
X-Original-To:
[email protected]
Delivered-To:
[email protected]
Received: by myservername.cloud (Postfix, from userid 30)
id A1F481050424; Mon, 8 Apr 2019 21:37:17 +0200 (CEST)
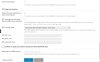
X-Original-To:
[email protected]
Delivered-To:
[email protected]
Received: from 97e5620e.skybroadband.com (97e5620e.skybroadband.com [151.229.98.14])
by myservername.cloud (Postfix) with ESMTP id 1BC78104F4C4
for <
[email protected]>; Mon, 8 Apr 2019 21:37:16 +0200 (CEST)
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=mydomain.com;
s=default; t=1554752236;
bh=xezQ7rJOVzmH7t03uUtXbHYURTC7yJ5hsFflJa1HcTg=; l=1797;
h=From:To:Subject;
b=KNtEFGngha1maV+awAO6VZOfNQYFRiNFtVjvfl3uLeJI88vKlCAeIASqo5UBX2AYC
Zrej0m+zXs1LQkejETGPf9XiOajd+RTWTbhX4+lNuxitoVsiovekhEbvd2pmgM13sF
av0MHT8kX9CFavWYljvTKpljNUhHI0rbV7x+eKQM=
Authentication-Results: myservername.cloud;
dmarc=pass (p=NONE sp=NONE) d=mydomain.com; header.from=mydomain.com;
dkim=pass
[email protected];
dmarc=pass (p=NONE sp=NONE) d=mydomain.com; header.from=mydomain.com;
dkim=pass
[email protected];
spf=fail (sender IP is 151.229.98.14)
[email protected] smtp.helo=97e5620e.skybroadband.com
Received-SPF: fail (myservername.cloud: domain of mydomain.com does not designate 151.229.98.14 as permitted sender) client-ip=151.229.98.14;
[email protected]; helo=97e5620e.skybroadband.com;
Message-ID: <
[email protected]>
Date: Mon, 08 Apr 2019 20:37:16 +0000
From: <
[email protected]>
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.2.17) Gecko/20110414 Thunderbird/3.1.10
MIME-Version: 1.0
To: <
[email protected]>