- Server operating system version
- Debian 10.12
- Plesk version and microupdate number
- 18.0.45
Can't access MariaDB 10.3.x on Plesk 18.0.45 on Debian 10.12 with "admin" - which is "root" user for MariaDB or MySQL in Plesk at least as i know!?
And remote connections are fully allowed on global MariaDB settings.
Screenshots HERE:
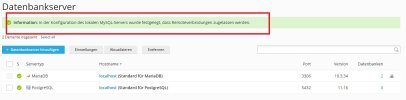
1.) Plesk global (Database independent) settings on "Tools & Settings" link:
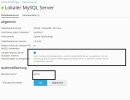
2.) HeidiSQL connection settings:
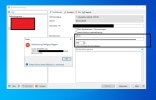
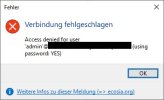
3.) Feedback when i try to connect:
...i tried to get the MariaDB root / admin from cat /etc/psa/.psa.shadow - as described HERE: Resolved - how to get the plesk obsidian mysql / mariadb (?) root-replacement user "admin" password?
But the password doesnt seem to be problem, more the IP whitelist. BUT WHY WTF if the checkbox for external access is activated on global settings config site for "admin" user!?
Bug??
Thank you very very much for your feedback(s).
And remote connections are fully allowed on global MariaDB settings.
Screenshots HERE:
1.) Plesk global (Database independent) settings on "Tools & Settings" link:

2.) HeidiSQL connection settings:

3.) Feedback when i try to connect:

...i tried to get the MariaDB root / admin from cat /etc/psa/.psa.shadow - as described HERE: Resolved - how to get the plesk obsidian mysql / mariadb (?) root-replacement user "admin" password?
But the password doesnt seem to be problem, more the IP whitelist. BUT WHY WTF if the checkbox for external access is activated on global settings config site for "admin" user!?
Bug??
Thank you very very much for your feedback(s).