We have continued the development of the popular Power Toys product, based on the request of many professionals from this domain. Thus we have launched version 4.8.0 with quite a lot of major enhancements and a few bug fixes.
The most of the requests have been about the possibility to write in vhost_ssl.conf as well, i.e. for https:// ... We have developped this functionality now in VHOST CONF writer, meaning that you may update both vhost.conf and vhost_ssl.conf.
We have enhanced the code generation as well for mod_suphp, thus those using Debian should not have any problems using the code. There seemed to be a few little differences on Debian, compared to CentOS, but it seems we have managed to eliminate them.
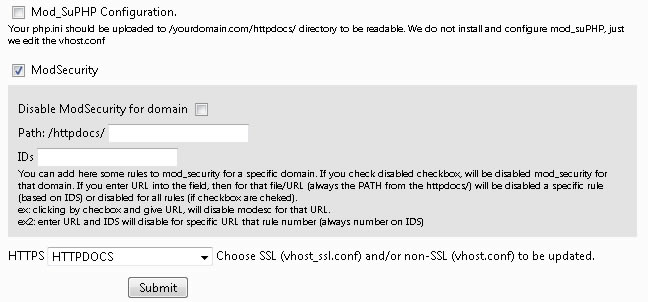
Mod_security .... yes, mod_security. And again, mod_security. We have introduced this tool to VHOST CONF. You may remember the times when your customers have complainde to get "Forbidden" and when checking the error logs (error_log) you have seen something like.
[Mon Dec 07 06:31:38 2009] [error] [client 190.97.219.4] ModSecurity: [file "/etc/httpd/modsecurity.d/50_asl_rootkits.conf"] [line "37"] [id "390144"] [rev "16"] [msg "Atomicorp.com WAF Rules: Command shell attack: Generic Attempt to remote include command shell"] [data ""] [severity "CRITICAL"] Access denied with code 403 (phase 2). Pattern match "(? gg|gopher|zlib|(?:ht|f)tps?)\\://(.+)\\.(?:c|dat|kek|gif|jpe?g|jpeg|png|sh|txt|bmp|dat|txt|js|html?|tmp|asp)\\x20?\\?" at REQUEST_URI. [hostname "www.grafxsoftware.com"] [uri "/product.php"] [unique_id "xYSV3LwoUk0AAGyZekUAAAAF"]
gg|gopher|zlib|(?:ht|f)tps?)\\://(.+)\\.(?:c|dat|kek|gif|jpe?g|jpeg|png|sh|txt|bmp|dat|txt|js|html?|tmp|asp)\\x20?\\?" at REQUEST_URI. [hostname "www.grafxsoftware.com"] [uri "/product.php"] [unique_id "xYSV3LwoUk0AAGyZekUAAAAF"]
Now it is simple, when your customer reports having a problem, you verify the error log, check whether his request is justified (as it's not always a false error) and if you decide, through Power Toys > Vhost Writer > Mod_security, you may deactivate the rule, not only on this URL (usually when having problems in admin/ ) but on the entie domain or on a specific IDS (in our example - 390144) . We are sure that this tool will be a very useful one.
Another enhancement is on the Outlook user settings part. We have introduced a possibility for the Admin part to specify the port on which the SMTP may be accessed. The reason is that the many local ISPs limit the access to port and thus another port is opened. In Admin on the Setup link, set the port, open in firewall (not included in Power Toys) and your users will have the registry files generated in that specific port.
Another bug solved. Domain expiry link, in PLESK 9 is different from PLESK 8.
More info
http://www.grafxsoftware.com/product.php/Power-Toys-for-PLESK/172/
For ideas, observations, etc ... please contact us
The most of the requests have been about the possibility to write in vhost_ssl.conf as well, i.e. for https:// ... We have developped this functionality now in VHOST CONF writer, meaning that you may update both vhost.conf and vhost_ssl.conf.
We have enhanced the code generation as well for mod_suphp, thus those using Debian should not have any problems using the code. There seemed to be a few little differences on Debian, compared to CentOS, but it seems we have managed to eliminate them.

Mod_security .... yes, mod_security. And again, mod_security. We have introduced this tool to VHOST CONF. You may remember the times when your customers have complainde to get "Forbidden" and when checking the error logs (error_log) you have seen something like.
[Mon Dec 07 06:31:38 2009] [error] [client 190.97.219.4] ModSecurity: [file "/etc/httpd/modsecurity.d/50_asl_rootkits.conf"] [line "37"] [id "390144"] [rev "16"] [msg "Atomicorp.com WAF Rules: Command shell attack: Generic Attempt to remote include command shell"] [data ""] [severity "CRITICAL"] Access denied with code 403 (phase 2). Pattern match "(?
Now it is simple, when your customer reports having a problem, you verify the error log, check whether his request is justified (as it's not always a false error) and if you decide, through Power Toys > Vhost Writer > Mod_security, you may deactivate the rule, not only on this URL (usually when having problems in admin/ ) but on the entie domain or on a specific IDS (in our example - 390144) . We are sure that this tool will be a very useful one.
Another enhancement is on the Outlook user settings part. We have introduced a possibility for the Admin part to specify the port on which the SMTP may be accessed. The reason is that the many local ISPs limit the access to port and thus another port is opened. In Admin on the Setup link, set the port, open in firewall (not included in Power Toys) and your users will have the registry files generated in that specific port.
Another bug solved. Domain expiry link, in PLESK 9 is different from PLESK 8.
More info
http://www.grafxsoftware.com/product.php/Power-Toys-for-PLESK/172/
For ideas, observations, etc ... please contact us
