JogoVogo
Basic Pleskian
- Server operating system version
- os_Debian 12.0
- Plesk version and microupdate number
- Plesk Obsidian v18.0.65_build1800241106.13
Good day everyone!
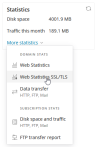
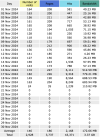
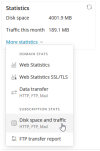
On our server, a domain generates about two terabytes of traffic daily.
It is a WP website whose graphics are quite small. There are also no unknown files in the directory(s).
In addition, the WA statistics do not make a reasonable statement about traffic. What is the most effective way to analyze them?
Cheers
Ron
On our server, a domain generates about two terabytes of traffic daily.
It is a WP website whose graphics are quite small. There are also no unknown files in the directory(s).
In addition, the WA statistics do not make a reasonable statement about traffic. What is the most effective way to analyze them?
Cheers
Ron