miguel.obando
New Pleskian
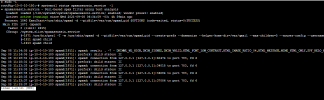
Watchdog is running since Aug 10, 2021 02:17 PM.
Watchdog is monitoring services:
Plesk Web Server
Plesk PHP Engine
Web Server (Apache)
SMTP Server (Postfix)
Dovecot IMAP and POP3 server
DNS Server (BIND)
MySQL
PostgreSQL
Plesk SpamAssassin
Plesk Postfix milter filter
Web Proxy Server (Nginx)
Fail2Ban authentication failure monitor
Watchdog is not monitoring disks.
Average CPU load: 11.2906%.
Average RAM usage: 4108208.2856.
Security scans number: 1.
Events:
[Sep 2, 2021 05:42 PM] 'Fail2Ban authentication failure monitor' service started.
[Sep 2, 2021 05:37 PM] 'Fail2Ban authentication failure monitor' service stopped.
[Aug 30, 2021 07:08 PM] 'SMTP Server (Postfix)' service started.
[Aug 30, 2021 07:08 PM] 'Fail2Ban authentication failure monitor' service started.
[Aug 30, 2021 07:08 PM] 'Web Proxy Server (Nginx)' service started.
[Aug 30, 2021 07:08 PM] 'Plesk SpamAssassin' service started.
[Aug 30, 2021 07:08 PM] 'PostgreSQL' service started.
[Aug 30, 2021 07:08 PM] 'MySQL' service started.
[Aug 30, 2021 07:08 PM] 'Web Server (Apache)' service started.
[Aug 30, 2021 07:08 PM] 'Plesk PHP Engine' service started.
[Aug 30, 2021 07:08 PM] 'Plesk Web Server' service started.
[Aug 30, 2021 06:39 AM] 'Plesk SpamAssassin' service started.
[Aug 30, 2021 06:34 AM] 'Plesk SpamAssassin' service stopped.
[Aug 30, 2021 01:00 AM] Security scanning report is in the file /opt/psa/var/modules/watchdog/report/security_2021-08-30.
Watchdog is monitoring services:
Plesk Web Server
Plesk PHP Engine
Web Server (Apache)
SMTP Server (Postfix)
Dovecot IMAP and POP3 server
DNS Server (BIND)
MySQL
PostgreSQL
Plesk SpamAssassin
Plesk Postfix milter filter
Web Proxy Server (Nginx)
Fail2Ban authentication failure monitor
Watchdog is not monitoring disks.
Average CPU load: 11.2906%.
Average RAM usage: 4108208.2856.
Security scans number: 1.
Events:
[Sep 2, 2021 05:42 PM] 'Fail2Ban authentication failure monitor' service started.
[Sep 2, 2021 05:37 PM] 'Fail2Ban authentication failure monitor' service stopped.
[Aug 30, 2021 07:08 PM] 'SMTP Server (Postfix)' service started.
[Aug 30, 2021 07:08 PM] 'Fail2Ban authentication failure monitor' service started.
[Aug 30, 2021 07:08 PM] 'Web Proxy Server (Nginx)' service started.
[Aug 30, 2021 07:08 PM] 'Plesk SpamAssassin' service started.
[Aug 30, 2021 07:08 PM] 'PostgreSQL' service started.
[Aug 30, 2021 07:08 PM] 'MySQL' service started.
[Aug 30, 2021 07:08 PM] 'Web Server (Apache)' service started.
[Aug 30, 2021 07:08 PM] 'Plesk PHP Engine' service started.
[Aug 30, 2021 07:08 PM] 'Plesk Web Server' service started.
[Aug 30, 2021 06:39 AM] 'Plesk SpamAssassin' service started.
[Aug 30, 2021 06:34 AM] 'Plesk SpamAssassin' service stopped.
[Aug 30, 2021 01:00 AM] Security scanning report is in the file /opt/psa/var/modules/watchdog/report/security_2021-08-30.