Is it possible somehow to tweak Fail2Ban log, to contain also which Wordpress instance was tried to log in, and Fail2Ban blocked it? That can be usefull if on server is hosted more then one Wordpress site.
For example, this morning, last 3 hours I have 208 tries to log in from different IP addresses, but I'm wondered what site is under attack.
At this moment is like this
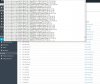
Now I will analyze access logs manually, but it would be much easier to have also site name included in this log.
Or at least here

This report we receiving on mail, should contain access log path, or site name, and which jail banned this IP. It is much useful then "3 attempts against default".
Did someone tried to set this, and how?
For example, this morning, last 3 hours I have 208 tries to log in from different IP addresses, but I'm wondered what site is under attack.
At this moment is like this

Now I will analyze access logs manually, but it would be much easier to have also site name included in this log.
Or at least here
This report we receiving on mail, should contain access log path, or site name, and which jail banned this IP. It is much useful then "3 attempts against default".
Did someone tried to set this, and how?
