No need to complicate things here, I'm well aware of the technical implications and limitations
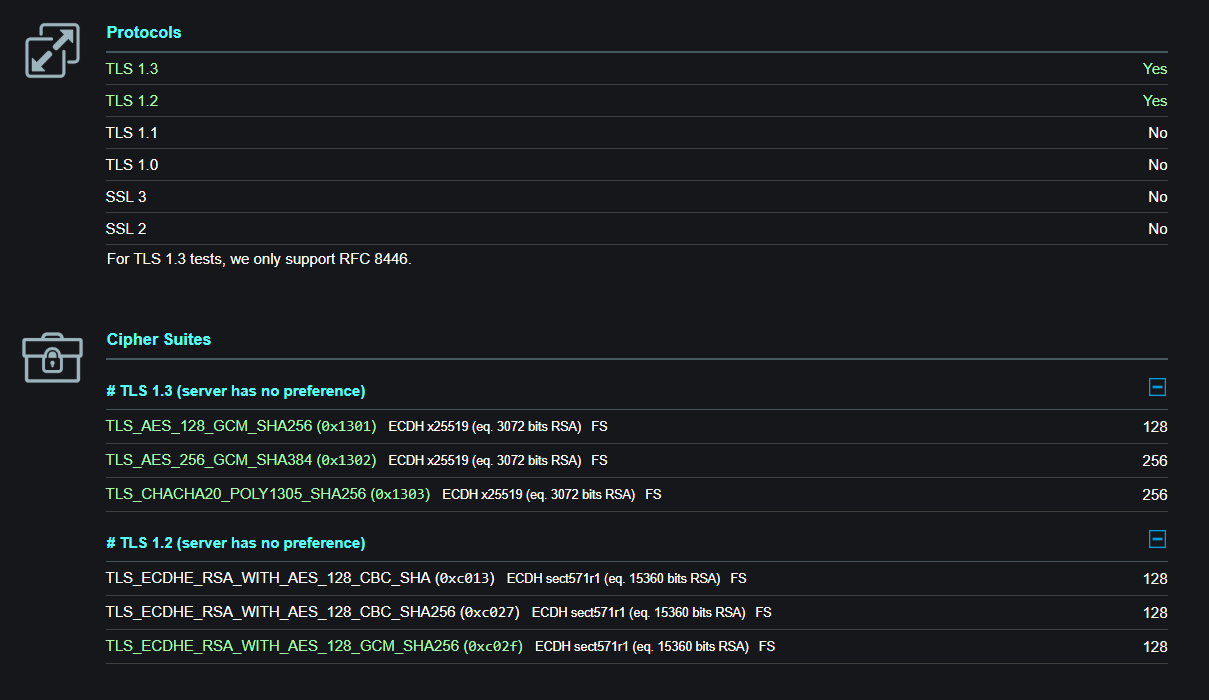
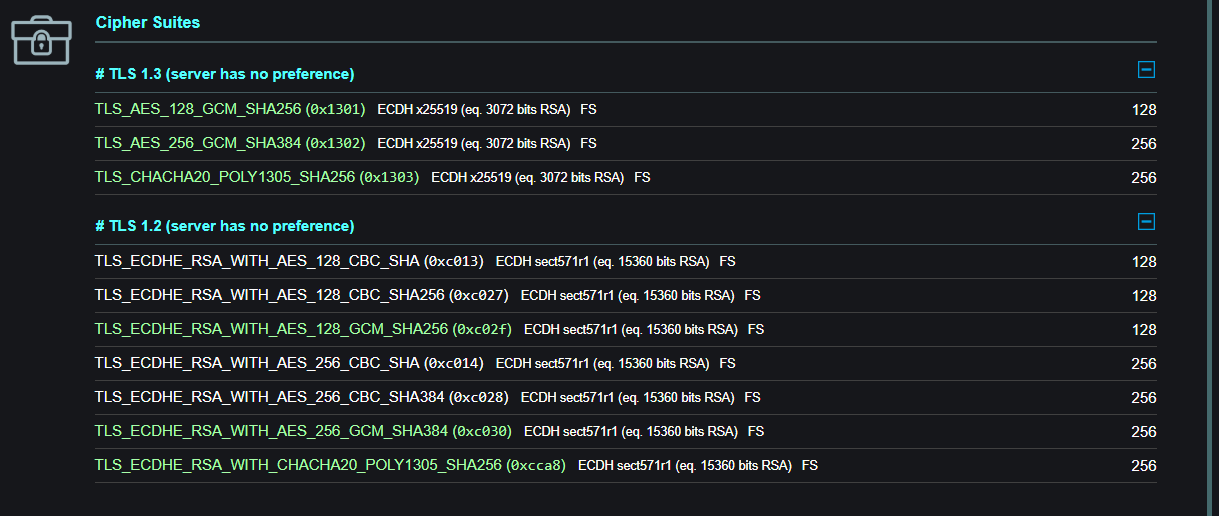
So I don't know why you even mention TLSv1.3, as it has clearly nothing to do with the current case?
Yes the whole problem is not limited to nginx, but rather anything that uses OpenSSL.
And technically it's currently not possible, to use different TLS protocols depending on domains/vhosts.
There simply exists no hook in OpenSSL for applications like nginx, apache2 or whatever, to determine/switch the configured/required TLS version based on the domain name
@ChristophRo
If you don't mind me saying so, but you are creating noise in the communication here and/or the topic thread as a whole.
First note that I talked about TLSv1.3, because your own output indicates clearly that you are testing with that protocol, even as negotiated protocol.
Furthermore, note that protocol negotation has nothing to do with server-side applications like Nginx or Apache.
In essence, server-side applications of the kind Nginx or Apache can be
compiled and/or configured to offer support for specific protocols, but actually
the web client (hence including browsers)
is determining the protocol that is factually used.
As such, OpenSSL is barely relevant, in the sense that it is
only relevant at (one the one hand) compilation time, in order to
allow certain protocols for server-side applications like Apache or Nginx and (on the other hand) the client-side, which client-side also has to be enabled to
support specific protocols.
There is a huge difference between "allow" (on the server-side) and "support" (on the client-side).
In summary, it does not matter how one wants to view or explain this protocol negotation, the facts remain that
- TLSv1.2 and TLSv1.1 are widely supported by default in both client-side and server-wide applications
- TLSv1.2 is widely preferred in both client-side and server-side applications
- TLSv1.2 is widely allowed in server-side applications
- TLSv1.3 is commonly (but not generally offered) in proper client-side applications
- TLSv1.3 is often not supported and/or not allowed in server-side applications, due to many issues with TLSv1.3
and note that the issues with TLSv1.3 are not related to server-side applications alone: in essence, the root cause of the majority of problems with TLSv1.3 are very closely related to OpenSSL and in particular the misalignment of OpenSSL with the commonly standards used by both server-side and client-side applications.
Simply stated, TLSv1.3 has never been working properly and development of client-side/server-side has never been able to grasp all (bug related) complexity of TLSv1.3.
And again, I can finish the above explanation with the statement:
it is and was always possible to allow (multiple) protocols on a per-domain/vhost basis.
Regards................