Plesk Obsidian 18.0.68 Web Host Edition here.
I'm reporting a major security and design inconsistency in how Plesk handles access control for the admin interface.
As part of the basic hardening process, I ensured that only essential ports — 80 and 443 — were exposed, as expected for a standard web server.
Since Plesk’s admin interface is officially documented to run on port 8443 and 8880, it was entirely reasonable to assume that administrative access would be strictly tied to that port.
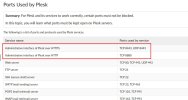
To secure the environment, I not only applied restrictions at the edge firewall level, but also configured Plesk’s own Tools & Settings > Firewall to allow access to the admin interface only from specific IP addresses.
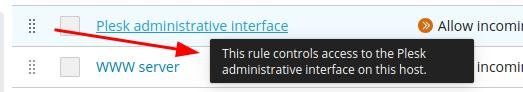
This setup clearly implies that the admin interface will be protected by that rule, and that such configuration should be sufficient to prevent unauthorized access to Plesk.
As previously stated, the admin interface is meant to be accessible only via port 8443 and 8880. Therefore, it’s entirely logical to expect that blocking that port for untrusted IPs would effectively make the admin interface inaccessible to them — as it should be. That’s the expected and logical behavior.
However, that's not the case. Apparently, someone thought it would be clever to proxy the admin interface through port 443, completely bypassing the expected security model.
If someone accesses the server directly via its IP address, Plesk serves a default page on port 443, which includes a link pointing to https://[server_ip]/login_up.php.
And that link? It exposes the full web admin interface — directly over port 443.
This behavior completely bypasses the firewall rule, since Plesk is internally proxying traffic and unintentionally exposing the admin interface through the default virtual host on port 443.So even with port 8443 and 8880 fully locked down to trusted IPs, anyone can still access the admin login page via HTTPS on port 443.
This design makes no sense.
It forces administrators to:- Manually configure “IP Access Restriction Management” (separate from the firewall), which is not clearly indicated as necessary.
- Understand that the firewall rules in Plesk do not actually restrict admin access, but only affect one specific port — 8443.
Expected fix:
- Stop proxying the admin interface through web server ports (80/443). Use a single, well-defined port for admin access only!
- Unify all admin access restrictions into a single mechanism that applies globally, across all entry points.
- Or at the very least, display a clear warning in the UI that the firewall rules alone do not protect the admin interface from exposure via alternate paths (such as the default host on port 443).

