blueberry
Basic Pleskian
I wanted to share a very bad thing that I found in my log today. A modsecurity rule of OWASP (WAF) was triggered on visits of Googlebot. I mean come on, if OWASP is not able to make the difference between an attacker and Googlebot, it makes no sense to install OWASP.
This is really something that I feared and it happened. This means we can't trust these modsecurity rules. (You want to use modsecurity? implement your custom rule sets). You don't want to use modsecurity? There are plenty of other solutions to protect your website via htaccess, nginx and your cms. We are in 2021, these free modsecurity rules are around since a while now and they still wonder whether Googlebot is an enemy? Come on it is not serious!
So beware!
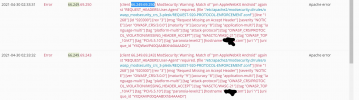
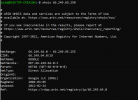
This is really something that I feared and it happened. This means we can't trust these modsecurity rules. (You want to use modsecurity? implement your custom rule sets). You don't want to use modsecurity? There are plenty of other solutions to protect your website via htaccess, nginx and your cms. We are in 2021, these free modsecurity rules are around since a while now and they still wonder whether Googlebot is an enemy? Come on it is not serious!
So beware!


