I currently have trouble to secure the Plesk updater which opens at port 8447 when I click "Updates" on the tools and settings page in the Plesk admin panel.
I migrated my server from Ubuntu 18.04 to 20.04 using the Plesk Migrator tonight and I'm now on Plesk Obsidian 18.0.39 Update 1.
Temporarily, I also migrated the 'archive' and 'live' folder of Letsencrypt to the new server using rsync.
After the migration, I regenerated all the Letsencrypt certificates and they are using the correct, new LE Certificate Chain.
In tools and settings, SSL/TLS settings, I chose the wildcard certificate of my domain to protect Plesk and the E-Mail System as well.
However, I have trouble to provide a proper certificate for the Updater.
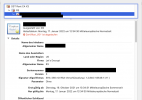
All websites, the mail system, the Plesk admin panel at port 8443, etc. are using the correct LE chain:
ISGR Root > R3 > mydomain.tld
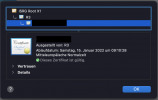
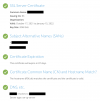
The Updater on port 8447, however, uses the following certificate and certificate chain and therefore, an SSL error occurs:
DST Root CA X3 (deprecated) > R3 (valid until 29. Sept. 2021) > mydomain.tld
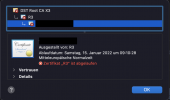
(URL is redacted in both screenshots)
With respect to the leaf certificate, the expiration date and time is the same and hence, I think its the correct certificate with the wrong chain.
How am I able to establish a secure connection to the updater again?
What I have tried yet:
I migrated my server from Ubuntu 18.04 to 20.04 using the Plesk Migrator tonight and I'm now on Plesk Obsidian 18.0.39 Update 1.
Temporarily, I also migrated the 'archive' and 'live' folder of Letsencrypt to the new server using rsync.
After the migration, I regenerated all the Letsencrypt certificates and they are using the correct, new LE Certificate Chain.
In tools and settings, SSL/TLS settings, I chose the wildcard certificate of my domain to protect Plesk and the E-Mail System as well.
However, I have trouble to provide a proper certificate for the Updater.
All websites, the mail system, the Plesk admin panel at port 8443, etc. are using the correct LE chain:
ISGR Root > R3 > mydomain.tld

The Updater on port 8447, however, uses the following certificate and certificate chain and therefore, an SSL error occurs:
DST Root CA X3 (deprecated) > R3 (valid until 29. Sept. 2021) > mydomain.tld

(URL is redacted in both screenshots)
With respect to the leaf certificate, the expiration date and time is the same and hence, I think its the correct certificate with the wrong chain.
How am I able to establish a secure connection to the updater again?
What I have tried yet:
- Regenerate all Letsencrypt certificates
- Chose another and re-chose the certificate for Plesk in tools and settings > SSL/TLS settings
- Verified, the old root certificate is not present anymore in /etc/ssl/certs
- Verified, the entry for the old root certificate is not present anymore in /etc/ca-certificates.conf (it's not commented out since it's not there at all)
- Ran 'update-ca-certificates'
- Added the following to the panel.ini
[ext-letsencrypt]
use-alternate-root = true - Started and Stopped the PSA Service
- Ran 'plesk repair installation'