itexpertnow
New Pleskian
Username:
TITLE
Plesk failed to protect from email spoofing
PRODUCT, VERSION, OPERATING SYSTEM, ARCHITECTURE
Ubuntu 22.4
Plesk Version 18.0.53
PROBLEM DESCRIPTION
Email Header Analyzer, RFC822 Parser - MxToolbox
STEPS TO REPRODUCE
ACTUAL RESULT
the email was not blocked
email copy
EXPECTED RESULT
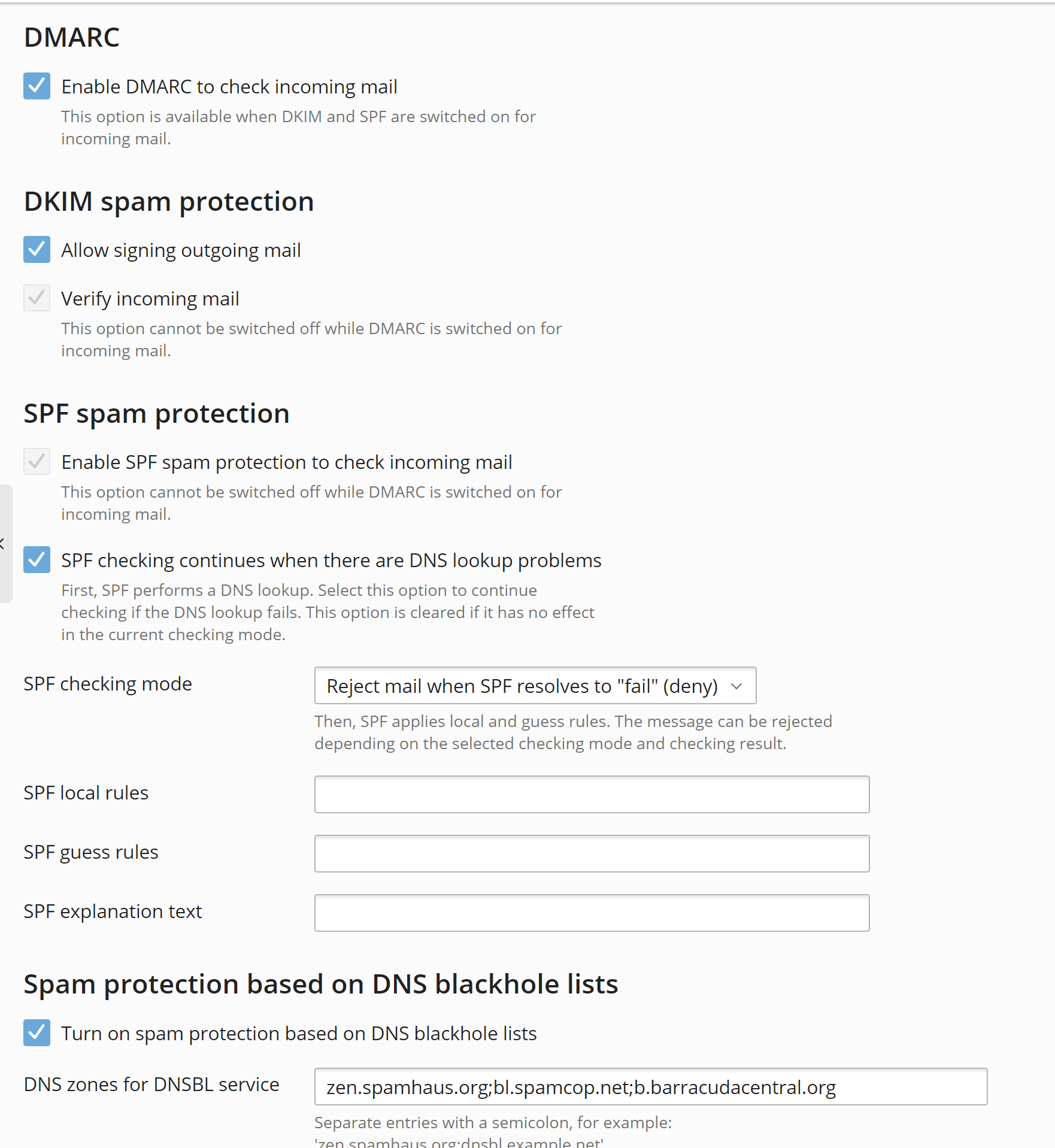
the email should be blocked because SPF softfail and the sender is not permitted sender
ANY ADDITIONAL INFORMATION
I added more restrictions in the postfix config but it didn't help much
# SMTP recipient restrictions
smtpd_recipient_restrictions =
permit_mynetworks,
permit_sasl_authenticated,
reject_unauth_destination,
reject_authenticated_sender_login_mismatch,
reject_invalid_hostname,
reject_non_fqdn_hostname,
reject_non_fqdn_sender,
reject_non_fqdn_recipient,
reject_unknown_sender_domain,
reject_unknown_recipient_domain,
reject_unlisted_recipient,
permit
YOUR EXPECTATIONS FROM PLESK SERVICE TEAM
Help with sorting out
TITLE
Plesk failed to protect from email spoofing
PRODUCT, VERSION, OPERATING SYSTEM, ARCHITECTURE
Ubuntu 22.4
Plesk Version 18.0.53
PROBLEM DESCRIPTION
Email Header Analyzer, RFC822 Parser - MxToolbox
STEPS TO REPRODUCE

ACTUAL RESULT
the email was not blocked
email copy
EXPECTED RESULT
the email should be blocked because SPF softfail and the sender is not permitted sender
ANY ADDITIONAL INFORMATION
I added more restrictions in the postfix config but it didn't help much
# SMTP recipient restrictions
smtpd_recipient_restrictions =
permit_mynetworks,
permit_sasl_authenticated,
reject_unauth_destination,
reject_authenticated_sender_login_mismatch,
reject_invalid_hostname,
reject_non_fqdn_hostname,
reject_non_fqdn_sender,
reject_non_fqdn_recipient,
reject_unknown_sender_domain,
reject_unknown_recipient_domain,
reject_unlisted_recipient,
permit
YOUR EXPECTATIONS FROM PLESK SERVICE TEAM
Help with sorting out
