- Server operating system version
- Ubuntu 22.04.5 LTS
- Plesk version and microupdate number
- Version 18.0.64 Web Admin Edition
Hello,
i have big issue with Plesk Firewall
I use Plesk on Hetzner dedicated server and have StorageBox with Hetzner with Samba enabled.
So I used to mount.cifs the storagebox on my server without any problems.
From yesterday I have started to use the Plesk Firewall and I can understand what am i doing wrong in setting the Firewall that once I enable it I cant access to my mounted storagebox anymore. I do not have any samba shared drives on my server, I just want to access to my remote storagebox via samba.
Hetzner supports both IPv4 and IPv6 protocols and my server, as well as storagebox has ipv4+ipv6 addresses.
Here is the debug which I have done so far
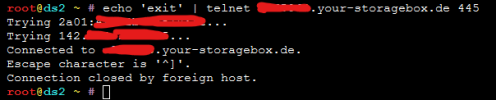
When Plesk Firewall is disabled I have this output from
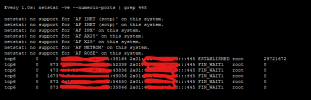
I see that connection from my server to storagebox is ESTABLISHED thru IPv6, and I can access my storagebox as always without any problems
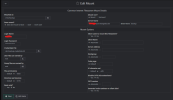
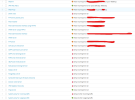
My Plesk Firewall is set with this rules
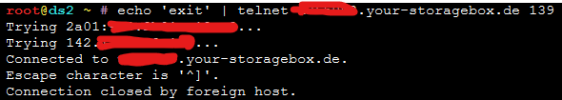
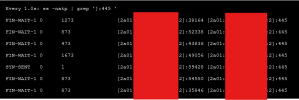
When I enable Plesk Firewall shortly after ESTABLISHED connections disappears and I get this output from
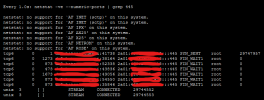
The SYN_SENT line comes for a second and goes off.
As I know in TCP, every SYN should get ACK to establish TCP connection and I understand ACK is not received for Samba SYN request and is blocked by firewall.
Shouldn't Plesk Firewall be stateless? It acts like a stateful firewall, since it seems to refuse the ACK for not denied outgoing connection.
Is there a way to fix this, maybe manually adding a rule?
Need extremely urgent help if possible.
Thank you all in advance for help.
Best regards.
i have big issue with Plesk Firewall
I use Plesk on Hetzner dedicated server and have StorageBox with Hetzner with Samba enabled.
So I used to mount.cifs the storagebox on my server without any problems.
From yesterday I have started to use the Plesk Firewall and I can understand what am i doing wrong in setting the Firewall that once I enable it I cant access to my mounted storagebox anymore. I do not have any samba shared drives on my server, I just want to access to my remote storagebox via samba.
Hetzner supports both IPv4 and IPv6 protocols and my server, as well as storagebox has ipv4+ipv6 addresses.
Here is the debug which I have done so far
When Plesk Firewall is disabled I have this output from
Bash:
watch -n 1 "netstat -ve --numeric-ports | grep 445"
I see that connection from my server to storagebox is ESTABLISHED thru IPv6, and I can access my storagebox as always without any problems
My Plesk Firewall is set with this rules

When I enable Plesk Firewall shortly after ESTABLISHED connections disappears and I get this output from
Bash:
watch -n 1 "netstat -ve --numeric-ports | grep 445"
The SYN_SENT line comes for a second and goes off.
As I know in TCP, every SYN should get ACK to establish TCP connection and I understand ACK is not received for Samba SYN request and is blocked by firewall.
Shouldn't Plesk Firewall be stateless? It acts like a stateful firewall, since it seems to refuse the ACK for not denied outgoing connection.
Is there a way to fix this, maybe manually adding a rule?
Need extremely urgent help if possible.
Thank you all in advance for help.
Best regards.