Fede Marsell
Basic Pleskian
Could you please elaborate on that question. I am not entirely sure I understand it. Sorry.
Once Imunify is installed —even without explicit permission— it begins scanning the server and uploading files it deems suspicious to external servers.
The extent of this behavior is unclear: it's not known whether Imunify uploads entire files or just fragments.
Regardless, this constitutes a serious security breach.
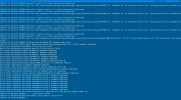
In the console.log, the data transfer is clearly visible:
imav.malwarelib.utils.malware_response: Uploaded file '/var/www/vhosts/domain.com/xxxx.php' to the Malware Response Service with reason: extended-
This is a critical issue — a data leak caused by the unauthorized installation of a third-party extension.