jamie!
New Pleskian
- Server operating system version
- AlmaLinux 9.3
- Plesk version and microupdate number
- 18.0.59
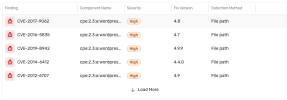
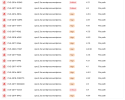
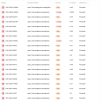
Wappspector is being picked up by security scanners. Of course they are false positives, but with the amount of servers, there are a ton. Ignoring/clearing the issues is a pain.
Is it possible to remove Wappspector -- and without unintended consequences?
Is it possible to remove Wappspector -- and without unintended consequences?