- Server operating system version
- Ubuntu 22.04.2 LTS
- Plesk version and microupdate number
- Plesk Obsidian Version 18.0.52
Hello everyone,
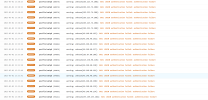
Although fail2ban is active, it does not block.
I always get attacked like this.
Which way do you follow to solve this and what do you do.
Thanks for a solution.
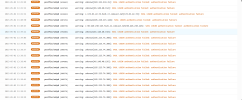
Although fail2ban is active, it does not block.
I always get attacked like this.
Which way do you follow to solve this and what do you do.
Thanks for a solution.
| 2023-05-02 13:46:16 | WARNING | postfix/smtpd [614764] | warning: unknown[46.148.40.155]: SASL LOGIN authentication failed: authentication failure |
| 2023-05-02 13:45:55 | WARNING | postfix/smtpd [614661] | warning: unknown[46.148.40.157]: SASL LOGIN authentication failed: authentication failure |
| 2023-05-02 13:45:48 | WARNING | postfix/smtpd [614764] | warning: unknown[46.148.40.150]: SASL LOGIN authentication failed: authentication failure |
| 2023-05-02 13:44:35 | WARNING | postfix/smtpd [614764] | warning: unknown[46.148.40.161]: SASL LOGIN authentication failed: authentication failure |
| 2023-05-02 13:43:54 | WARNING | postfix/smtpd [614661] | warning: unknown[46.148.40.164]: SASL LOGIN authentication failed: authentication failure |
| 2023-05-02 13:43:34 | WARNING | postfix/smtpd [614764] | warning: unknown[46.148.40.160]: SASL LOGIN authentication failed: authentication failure |