- Server operating system version
- windows server 2022
- Plesk version and microupdate number
- plesk obsidian 18.0.71
Hello Plesk Team & Community,
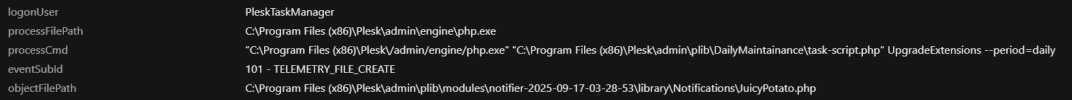
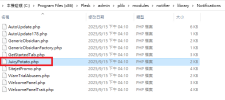
I recently discovered a file named JuicyPotato.php in the following directory on our Windows server:C:\Program Files (x86)\Plesk\admin\plib\modules\notifier\library\Notifications\
Given that "JuicyPotato" is a known name for a privilege escalation tool, finding a file with this name is a security concern for us.
I would like to clarify a few things:
Thank you.
P.S
1.Plesk version: plesk obsidian 18.0.71
2.OS: windows server 2022
I recently discovered a file named JuicyPotato.php in the following directory on our Windows server:C:\Program Files (x86)\Plesk\admin\plib\modules\notifier\library\Notifications\
Given that "JuicyPotato" is a known name for a privilege escalation tool, finding a file with this name is a security concern for us.
I would like to clarify a few things:
- Is this file a legitimate part of a standard Plesk installation or one of its official modules?
- If it is a legitimate file, what is its intended purpose and functionality?
- If this is not an official Plesk file, what is the recommended procedure for its removal and for checking if the system has been otherwise compromised?
Thank you.

P.S
1.Plesk version: plesk obsidian 18.0.71
2.OS: windows server 2022