DennisAm
Basic Pleskian
TITLE:
ACTUAL RESULT:
SSL Wildcard renewal not working with DNS service disabled
PRODUCT, VERSION, OPERATING SYSTEM, ARCHITECTURE:Version 17.8.11 Update #67, CentOS Linux 7.6.1810 (Core), SSL It! 1.1.1-521
PROBLEM DESCRIPTION:I can issue wildcard SSL certificates without issues in SSL It when the DNS Service on the server is disabled, but autorenewal doesn't seem to work, as we keep getting these emails mentioning that autorenewal failed:

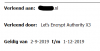
The certificate validity mentioned in the email (81 days) matches the one on the certificate (1-12-2019):
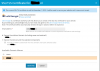
When I try to renew the certificate manually through SSL It!, I go through the "Reissue certificate screen":
I then am asked again to set up the DNS record (which exactly matches the one I've already set, so I can just click "Reload"):

The certificate is then renewed/installed without any problems:

So, there seems to be a problem in the automated renewal of SSL certificates through the SSL It! extension when the DNS Service on the server is disabled/removed.
STEPS TO REPRODUCE:The certificate validity mentioned in the email (81 days) matches the one on the certificate (1-12-2019):

When I try to renew the certificate manually through SSL It!, I go through the "Reissue certificate screen":

I then am asked again to set up the DNS record (which exactly matches the one I've already set, so I can just click "Reload"):

The certificate is then renewed/installed without any problems:
So, there seems to be a problem in the automated renewal of SSL certificates through the SSL It! extension when the DNS Service on the server is disabled/removed.
- Disable/remove the DNS server server-wide through Updates and Upgrades
- Issue a wildcard certificate for a domain, you will be asked to set up a DNS record for _acme-challenge.YOURDOMAIN.TLD
- Validate the DNS record; your certificate will be issued successfully and will have a validity of 3 months.
- Wait some days until Plesk tries to renew the certificate automatically; you will receive the email as mentioned above ("Could not renew - DNS service is not enabled"). You will get this email (almost) every day again.
- Renewing the certificate manually through the Plesk/SSL It! extension works without any problems.
Domain wildcard certificate auto-renewal throws an error and sends an email to the admin that the DNS Service on the server isn't enabled.
EXPECTED RESULT:Domain wildcard certificate auto-renews without any problems.
ANY ADDITIONAL INFORMATION:
YOUR EXPECTATIONS FROM PLESK SERVICE TEAM:Confirm bug
Last edited:
