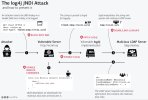
Good evening everyone!
I only have the question if I should care because of the actual zero day exploit about log4j.
I heard that apache is vulnerable, too.
Now my question is: Do I have to update Plesk because of this zero day exploit?
It is friday and I hope that I dont need to now and that I can run the updates on monday!
Thank you for answers!
Goodfred
I only have the question if I should care because of the actual zero day exploit about log4j.
I heard that apache is vulnerable, too.
Now my question is: Do I have to update Plesk because of this zero day exploit?
It is friday and I hope that I dont need to now and that I can run the updates on monday!
Thank you for answers!
Goodfred