I want to say that we know about this issue and hear you.
We tried to find a proper solution for this issue but have no luck on the way.
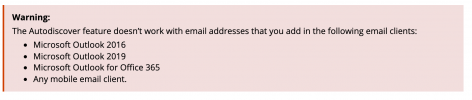
Mail Autodiscover works well for old mail clients like Outlook 2016 but facing issues with the auto-configuration of Microsoft O365/2019 mail clients. The issue exists because these mail clients do not request a mail configuration directly from a Plesk server but instead using Microsoft cache servers for such purposes.
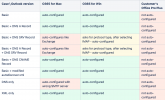
Also, it's important to note that the issue exists mostly for MS Office Pro mail clients, based on our tests of possible configurations:
Microsoft Support suggested for us reactive solution only: when mail autodiscover failed for a customer, you can
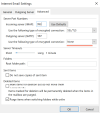
bypass using an MS proxy server by adding a registry key to the Outlook client (using Registry on a local machine):
-----
HKEY_CURRENT_USER\Software\Microsoft\Office\x.0\Outlook\AutoDiscover
Name : ExcludeExplicitO365Endpoint
Value : 1
------
Then a mail configuration will be requested directly from a Plesk server.
This solution is not suitable for us, but it's the best that we have for now. We continue communication with Microsoft with the hope of solving the issue.
But preliminary summary, that the new Outlook doesn't support autodiscovery for non-MS services (not Exchange servers).
We tried to find a proper solution for this issue but have no luck on the way.
Mail Autodiscover works well for old mail clients like Outlook 2016 but facing issues with the auto-configuration of Microsoft O365/2019 mail clients. The issue exists because these mail clients do not request a mail configuration directly from a Plesk server but instead using Microsoft cache servers for such purposes.
Also, it's important to note that the issue exists mostly for MS Office Pro mail clients, based on our tests of possible configurations:

Microsoft Support suggested for us reactive solution only: when mail autodiscover failed for a customer, you can
bypass using an MS proxy server by adding a registry key to the Outlook client (using Registry on a local machine):
-----
HKEY_CURRENT_USER\Software\Microsoft\Office\x.0\Outlook\AutoDiscover
Name : ExcludeExplicitO365Endpoint
Value : 1
------
Then a mail configuration will be requested directly from a Plesk server.
This solution is not suitable for us, but it's the best that we have for now. We continue communication with Microsoft with the hope of solving the issue.
But preliminary summary, that the new Outlook doesn't support autodiscovery for non-MS services (not Exchange servers).