Alex Presland
Basic Pleskian
- Server operating system version
- Ubuntu 22.04.3 LTS
- Plesk version and microupdate number
- Obsidian 18.0.57 Update #4
I'm running Plesk Obsidian 18.0.57 Update #4 on Ubuntu 22.04.3 LTS. This server was built in February 2023 from the AWS template. Under "Add and Remove Product Components" it shows that we're running Postfix [3.6.4-1ubuntu1-1] as the mail server, SpamAssassin [3.4.6-1ubuntu0.22.04.1], and Dovecot [2.3.21-v.ubuntu.22.04+p18.0.57.0+t231106.2014] for the IMAP/POP3 servers. The only extension which I think is relevant to email is Warden Anti-spam and Virus Protection [Version 4.00-1] by @danami .
I don't know whether this is a bug with Plesk, Warden, or a configuration issue, so I'm raising it here for discussion before submitting a bug report.
Some users have been complaining that some of their emails which are being forwarded through the server are sometimes being rejected by certain destinations. For the most part it works perfectly. Until now I've been unable to replicate this, but one affected user spotted that whenever they attached a DOCX or XLSX file it was rejected by certain destinations, but other attachments like PDF & JPG would go through without issue.
I have set up a test scenario and have successfully reproduced the issue and captured the email at various points on its journey. All emails were sent from "Microsoft Outlook for Microsoft 365 MSO (Version 2311 Build 16.0.17029.20028) 64-bit"
Sending an HTML email (with no attachments) in to the Original Destination is successful and all forwarding recipients receive it.
TEST 2
Sending an HTML email (with a PDF attachment) in to the Original Destination is successful and all forwarding recipients receive it.
TEST 3
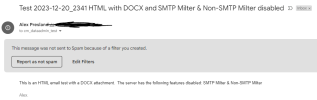
Sending an HTML email with a DOCX attachment in to the Original Destination is partially successful. It ends up in the Original Destination mailbox, the different domain mailbox on the same Plesk server, BT Internet, and the mailbox on the source server. It is rejected by Yahoo, TalkTalk, iCloud and Hotmail... all giving the reason that the DMARC validation failed. Where it made into a mailbox (instead of being rejected) it shows a DMARC fail.
I ssh-ed into the Plesk server and retrieved the email from /var/qmail/mailnames/[DOMAIN]/[LOCAL_PART]/Maildir/new/ for both the Original Destination and the different domain on the same Plesk server. Back on my PC I used WinMerge to compare them. I was shocked to find that the email forwarded within Plesk was failing DKIM & DMARC. Below are some snippets from the email headers explaining why for both "Original" and "Forwarded".
The first thing that I spotted was that a "Received" header had been line-wrapped:
Original
Next were the Authentication-Results...
Original
In the header of the forwarded email the reason for this is given (note the reason in red!):
So now looking at the body portions of the email I spotted the line-wrapping of the "Content-Type" of the MS Word document:
Original
A PDF will have the following Content-Type... so won't be wrapped and won't fail DKIM / DMARC when forwarded.
So... a number of questions:

I don't know whether this is a bug with Plesk, Warden, or a configuration issue, so I'm raising it here for discussion before submitting a bug report.
Some users have been complaining that some of their emails which are being forwarded through the server are sometimes being rejected by certain destinations. For the most part it works perfectly. Until now I've been unable to replicate this, but one affected user spotted that whenever they attached a DOCX or XLSX file it was rejected by certain destinations, but other attachments like PDF & JPG would go through without issue.
I have set up a test scenario and have successfully reproduced the issue and captured the email at various points on its journey. All emails were sent from "Microsoft Outlook for Microsoft 365 MSO (Version 2311 Build 16.0.17029.20028) 64-bit"
- EMAIL SOURCE: An email address outside the Plesk server coming from a domain with a DMARC record containing "p=reject"
- EMAIL ORIGINAL DESTINATION: An email address on the Plesk server with mailbox enabled and multiple forwarding destinations
- EMAIL FORWARDING DESTINATIONS (8 of them!): Another mailbox on the Plesk server, but under a different domain; Gmail; Yahoo; BT Internet; TalkTalk; iCloud; Hotmail; and a mailbox back on the source server)
Sending an HTML email (with no attachments) in to the Original Destination is successful and all forwarding recipients receive it.
TEST 2
Sending an HTML email (with a PDF attachment) in to the Original Destination is successful and all forwarding recipients receive it.
TEST 3
Sending an HTML email with a DOCX attachment in to the Original Destination is partially successful. It ends up in the Original Destination mailbox, the different domain mailbox on the same Plesk server, BT Internet, and the mailbox on the source server. It is rejected by Yahoo, TalkTalk, iCloud and Hotmail... all giving the reason that the DMARC validation failed. Where it made into a mailbox (instead of being rejected) it shows a DMARC fail.
I ssh-ed into the Plesk server and retrieved the email from /var/qmail/mailnames/[DOMAIN]/[LOCAL_PART]/Maildir/new/ for both the Original Destination and the different domain on the same Plesk server. Back on my PC I used WinMerge to compare them. I was shocked to find that the email forwarded within Plesk was failing DKIM & DMARC. Below are some snippets from the email headers explaining why for both "Original" and "Forwarded".
The first thing that I spotted was that a "Received" header had been line-wrapped:
Original
Forwarded:Received: from [12.34.56.78] (helo=DESKTOP3B)
by sending.server.name with esmtpsa (TLS1.2) tls TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
(Exim 4.96)
(envelope-from <[email protected]>)
id 1rFgTU-00Gg51-1D
for [email protected];
Tue, 19 Dec 2023 20:13:56 +0000
Received: from [12.34.56.78] (helo=DESKTOP3B)
by sending.server.name with esmtpsa (TLS1.2) tls
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
(Exim 4.96)
(envelope-from <[email protected]>)
id 1rFgTU-00Gg51-1D
for [email protected];
Tue, 19 Dec 2023 20:13:56 +0000
Next were the Authentication-Results...
Original
Forwarded (note the "dkim=fail" in red!)Authentication-Results: destination.server;
dmarc=pass (p=REJECT sp=NONE) smtp.from=sending.domain header.from=sending.domain;
dkim=pass header.d=sending.domain;
spf=pass (sender IP is 23.45.67.89) smtp.mailfrom=[email protected] smtp.helo=sending.server.name
Authentication-Results: destination.server;
dmarc=pass (p=REJECT sp=NONE) smtp.from=sending.domain header.from=sending.domain;
dkim=pass header.d=pubupdates.camra.org.uk;
dkim=fail header.d=sending.domain;
spf=pass (sender IP is 127.0.0.1) smtp.mailfrom=srs0=1nt2=h6=sending.domain=[email protected] smtp.helo=localhost
In the header of the forwarded email the reason for this is given (note the reason in red!):
Authentication-Results: destination.server (amavisd-new);
dkim=pass (1024-bit key) header.d=destination.domain
header.b="RZMWSriP"; dkim=fail (1024-bit key)
reason="fail (body has been altered)" header.d=sending.domain
header.b="i4IxasB+"
So now looking at the body portions of the email I spotted the line-wrapping of the "Content-Type" of the MS Word document:
Original
Forwarded------=_NextPart_000_0267_01DA32B7.E5AFD240
Content-Type: application/vnd.openxmlformats-officedocument.wordprocessingml.document;
name="Adding Account to Gmail_Rev1.0.docx"
Content-Transfer-Encoding: base64
Content-Disposition: attachment;
filename="Adding Account to Gmail_Rev1.0.docx"
------=_NextPart_000_0267_01DA32B7.E5AFD240
Content-Type:
application/vnd.openxmlformats-officedocument.wordprocessingml.document;
name="Adding Account to Gmail_Rev1.0.docx"
Content-Transfer-Encoding: base64
Content-Disposition: attachment;
filename="Adding Account to Gmail_Rev1.0.docx"
A PDF will have the following Content-Type... so won't be wrapped and won't fail DKIM / DMARC when forwarded.
Content-Type: application/pdf;
So... a number of questions:
- Is there a configuration setting that I can change to fix this, or do people think that this is a bug which I should report formally?
- If a configuration tweak, can this be the out-of-the-box behaviour
- Is anyone able to reproduce this issue on their Plesk server?