Hope this is the right place to post this question.
Our server is running; Plesk 11.0.9 and CentOS 5.7 it has a Q8200 CPU @ 2.33GHz and 2GB of RAM. Now there are just two websites on the server plus a couple of redirects/forwarding domains, although lots of domains are still on the server but turned off in Plesk. Both websites are OSCommerce sites and I just need to keep these sites going until the end of the year when we will switch to our new Joomla based website.
Sadly our web designer who was the guy who last maintained the server, passed away at the beginning of the year and I have had to step in and from knowing nothing about LINUX servers have been frantically learning as much as I could but now I seem to have reached the end of my abilities !!
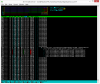
We have seen an increasing number of server crashes and after various checks of the logs, fitting a new BIOS battery, check of the hardware by EasySpace who host the server, installation of ClamAV, LMD and RKHunter (which did find some Trojans and Suspect software), I have traced it down to some external Http activity that is taking all of my CPU time and RAM. Here is a screen capture of the Htop listing and when I killed these processes the CPU and RAM went back to normal. The problem is that I usually have to restart the HTTPD service and sometimes things get so bad that the server crashes and I have to request a power cycle.
Frankly it is driving me crazy and I just do not know what to do next - any ideas ? Are there any extensions for Plesk that might help ?
Our server is running; Plesk 11.0.9 and CentOS 5.7 it has a Q8200 CPU @ 2.33GHz and 2GB of RAM. Now there are just two websites on the server plus a couple of redirects/forwarding domains, although lots of domains are still on the server but turned off in Plesk. Both websites are OSCommerce sites and I just need to keep these sites going until the end of the year when we will switch to our new Joomla based website.
Sadly our web designer who was the guy who last maintained the server, passed away at the beginning of the year and I have had to step in and from knowing nothing about LINUX servers have been frantically learning as much as I could but now I seem to have reached the end of my abilities !!
We have seen an increasing number of server crashes and after various checks of the logs, fitting a new BIOS battery, check of the hardware by EasySpace who host the server, installation of ClamAV, LMD and RKHunter (which did find some Trojans and Suspect software), I have traced it down to some external Http activity that is taking all of my CPU time and RAM. Here is a screen capture of the Htop listing and when I killed these processes the CPU and RAM went back to normal. The problem is that I usually have to restart the HTTPD service and sometimes things get so bad that the server crashes and I have to request a power cycle.
Frankly it is driving me crazy and I just do not know what to do next - any ideas ? Are there any extensions for Plesk that might help ?

