Nextgen-Networks
Basic Pleskian
- Server operating system version
- Ubuntu 20.04.6 LTS
- Plesk version and microupdate number
- Plesk Obsidian Version 18.0.56 Update #4
Hello Plesk users and Plesk Team,
I face a strange situation since a couple of days.
Existing Lets Encrypt certificates can't be renewed (was working for 2 years).
I've tried several checks to assure everything on server and domain side is configured properly.
... and left confused about the situation.
This is the error message I was confronted with::
Then wrote a short script to verify the external availability of that acme-challenge file:
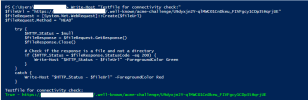
Looks good ...
Next tried to renew the certificate with disabled firewall and web-application firewall.
Result is still the same - no renew possible.
Anyone else wit the same situation or preferred: With a solution? :-D
I face a strange situation since a couple of days.
Existing Lets Encrypt certificates can't be renewed (was working for 2 years).
I've tried several checks to assure everything on server and domain side is configured properly.
... and left confused about the situation.
This is the error message I was confronted with::
SSL/TLS-Zertifikat konnte für myDomain.TLD nicht ausgestellt werden.
Details:
Let's Encrypt-SSL/TLS-Zertifikat konnte nicht ausgestellt werden für myDomain.TLD. Die Autorisierung dieser Domain ist fehlgeschlagen.
Details
Invalid response from https://acme-v02.api.letsencrypt.org/acme/authz-v3/UID.
Details:
Type: urn:ietfarams:acme:error:connection
Status: 400
Detail: 89.22.113.48: Fetching https://myDomain.TLD/.well-known/acme-challenge/U9dyxjn2Y-qlMWC01CnDkeu_FIVFgcy1CDp35HqrjUE: Timeout during connect (likely firewall problem)
Then wrote a short script to verify the external availability of that acme-challenge file:

Looks good ...
Next tried to renew the certificate with disabled firewall and web-application firewall.
Result is still the same - no renew possible.
Anyone else wit the same situation or preferred: With a solution? :-D