- Server operating system version
- Ubuntu 18.04.6 LTS
- Plesk version and microupdate number
- 18.0.52 Update #3,
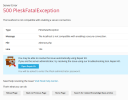
Hi, I'm attempting to enable MySQL secure connection on 18.0.52 but when I edit panel.ini with tls.enable to true Plesk gives the following fatal error "The localhost is not compatible with enabling a secure connection." This plesk instance is connected to a localhost instance and one remote instance of MySQL 5.7. My best guess is that the fatal is displayed because the two DBs mentioned don't have require_secure_transport=ON configured yet BUT it's not obvious what the error message is referring to. Any tips?
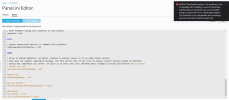
Panel.ini edit:
[database]
tls.enable = true;
Panel.ini edit:
[database]
tls.enable = true;