Dukemaster
Regular Pleskian
Hi, Plesk friends,
I want to improve SSL-integration by OCSP stapling for each domain.
Therefor I found an older thread with really good help by @Lloyd_mcse and @UFHH0.
So I followed these instructions by this way:
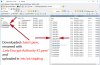
1. First I created "stapling" folder in
2. Downloaded one domain chain.pem file and (re)named it to "Lets-Encrypt-Authority-X1.pem".
4. For the the last step I added
to Domains > domain.tld > Apache & Nginx Settings > Additional nginx directives
The result for all domains secured by Letsencrypt on SSLlabs.com seems to be OK for (only) 1st certificate).
But I'm not sure if I've done everything what is needed.
Because in this thread @UFHH01 wrote about the integration of the fullchain.pem file. And I'm also unsure about the fact that @Lloyd_mcse said:
And the content of it is only one certificate code, not two?
Did I make a mistake or forget something else according to this two certificates?
Lots of greets
I want to improve SSL-integration by OCSP stapling for each domain.
Therefor I found an older thread with really good help by @Lloyd_mcse and @UFHH0.
So I followed these instructions by this way:
1. First I created "stapling" folder in
Code:
/etc/ssl/staplingBy comparing chain.pem files I realized that the content of the chain.pem file is always the same for all domains. Or in other words all domains have the same content of chain.pem.
3. Then I uploaded the new Lets-Encrypt-Authority-X1.pem (former chain5.pem) to
Code:
/etc/ssl/stapling
Code:
ssl_stapling on;
ssl_stapling_verify on;
ssl_trusted_certificate /etc/ssl/stapling/Lets-Encrypt-Authority-X1.pem;
resolver 8.8.4.4 8.8.8.8 valid=300s;
resolver_timeout 10s;The result for all domains secured by Letsencrypt on SSLlabs.com seems to be OK for (only) 1st certificate).
But I'm not sure if I've done everything what is needed.
Because in this thread @UFHH01 wrote about the integration of the fullchain.pem file. And I'm also unsure about the fact that @Lloyd_mcse said:
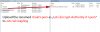
As you can see on my second screenshot, I've only the Lets-Encrypt-Authority-X1.pem in folder "stapling".containing the Intermediate (Let's Encrypt Authority X3) and the Root CA (DST Root CA X3) and upload them to the folder
And the content of it is only one certificate code, not two?
Did I make a mistake or forget something else according to this two certificates?
Lots of greets

Last edited:
