Peter Carlsson
Basic Pleskian
When i ssh and run npm i get root as owner and my app brakes. I need to ssh as a customer to run npm build and i have added customer ssh user but i get:
Permission denied (publickey,gssapi-keyex,gssapi-with-mic)
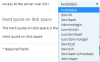
Under: Access to the server over SSH
i also have a lot of options other than Forbidden, what should i choose?
Please advise.
Permission denied (publickey,gssapi-keyex,gssapi-with-mic)
Under: Access to the server over SSH
i also have a lot of options other than Forbidden, what should i choose?
Please advise.